Bamboocloud Intelligent Risk Identification
helps your enterprise to easily cope with the following challenges
-
Abnormal user behaviors
 How to detect anomalous user behavior when accessing internal applications, data, or services?
How to detect anomalous user behavior when accessing internal applications, data, or services? -
Persistent brute force attacks
 How to prevent ongoing password-cracking attempts and identity spoofing attacks?
How to prevent ongoing password-cracking attempts and identity spoofing attacks? -
Increasing regulatory demands for identity security
 How to quickly meet evolving compliance requirements with a centralized risk control and auditing system—for proactive alerts, real-time controls, and post-incident traceability?
How to quickly meet evolving compliance requirements with a centralized risk control and auditing system—for proactive alerts, real-time controls, and post-incident traceability? -
Insider threats remain hidden
 How to track and audit internal users attempting to bypass controls to access key assets?
How to track and audit internal users attempting to bypass controls to access key assets? -
Complex access environments
 How to secure access to sensitive data when users connect from various locations, networks, and devices?
How to secure access to sensitive data when users connect from various locations, networks, and devices? -
Escalating external threats
 How to effectively defend against both high-frequency attacks and sophisticated, low-frequency intrusions from hackers?
How to effectively defend against both high-frequency attacks and sophisticated, low-frequency intrusions from hackers?
What is AI risk identification
Bamboocloud’s AI-powered risk identification solution serves as the “brain” of your IAM ecosystem—analyzing ongoing and potential risks in real time. Leveraging adaptive risk identification, our platform instantly flags identity, permission, and access risks, empowering your business to prevent threats proactively, block risks as they occur, and trace incidents post-event.
Overview
Solution Overview
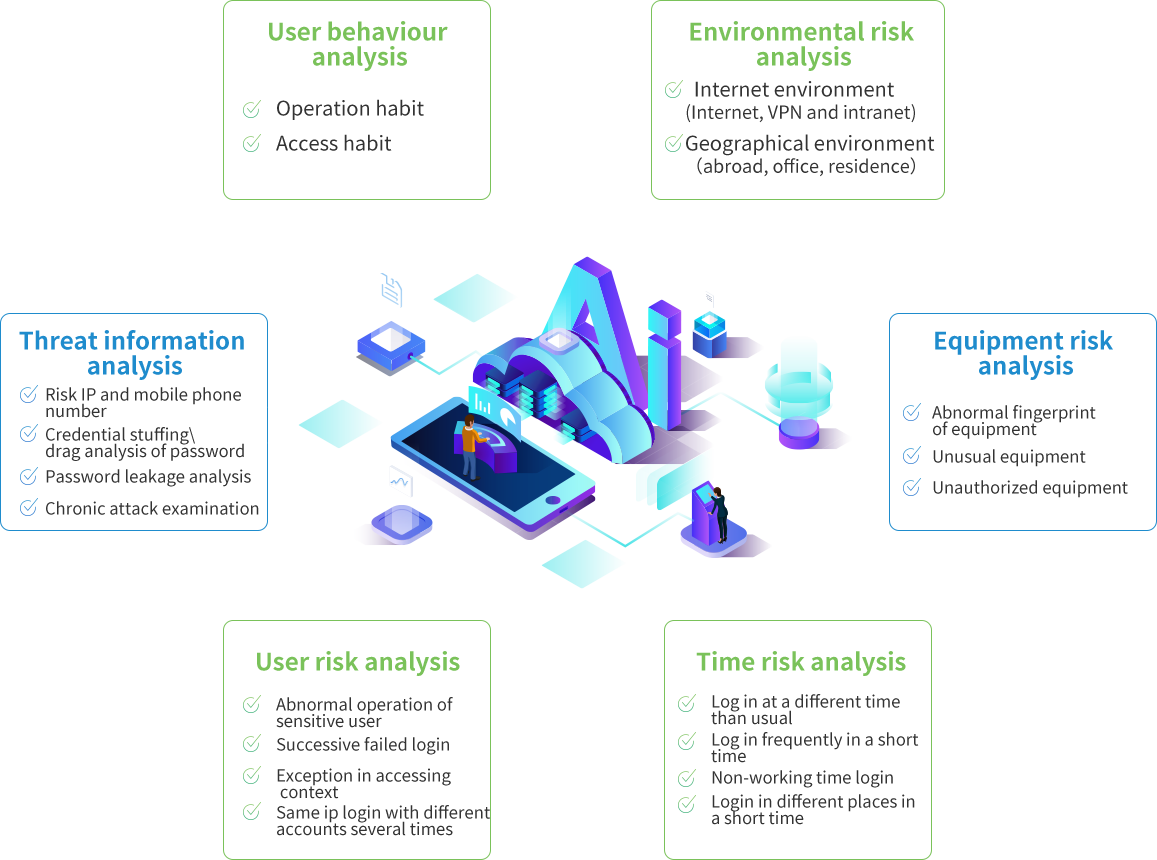
Solution Architecture
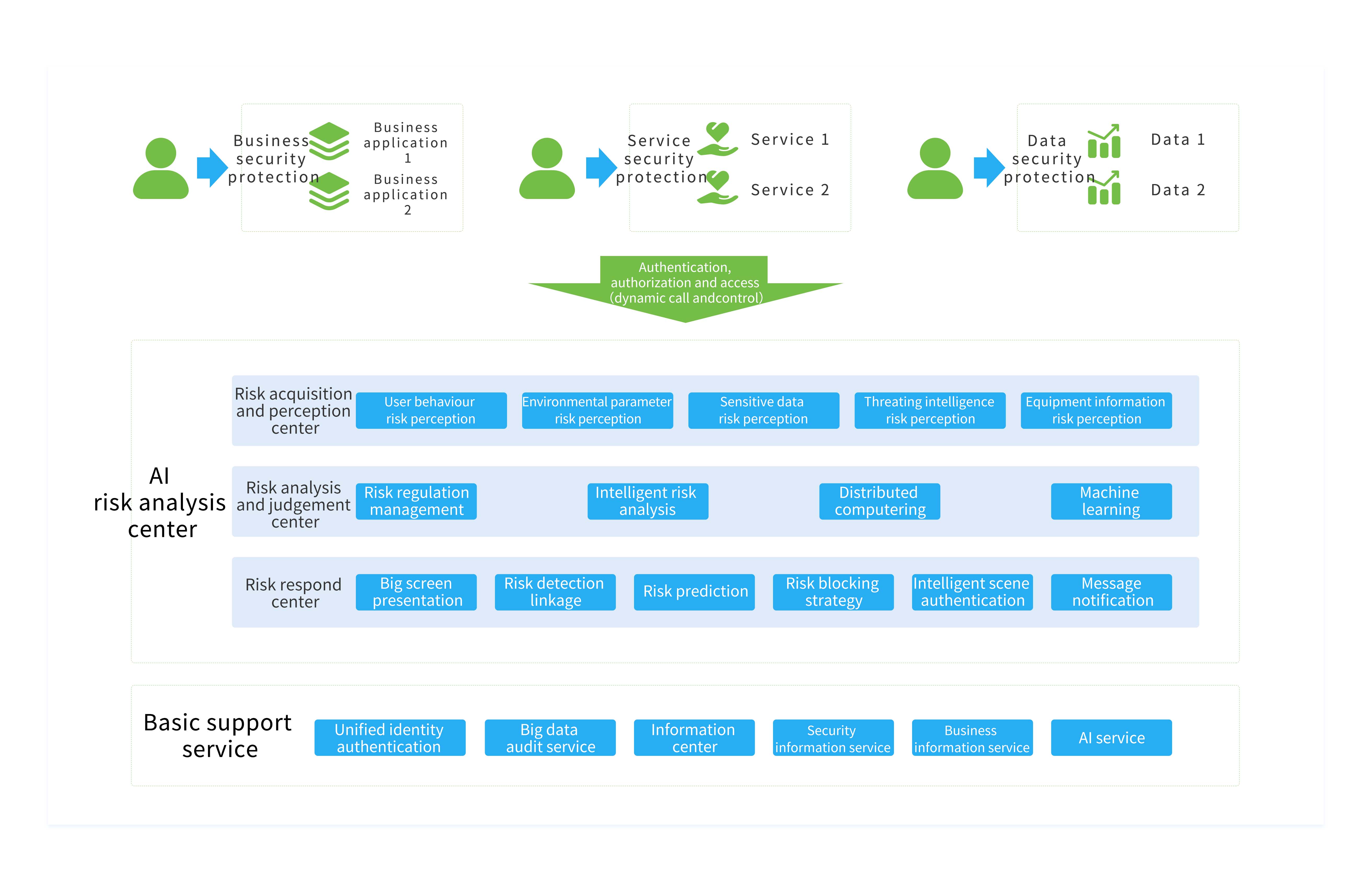
Solution Features
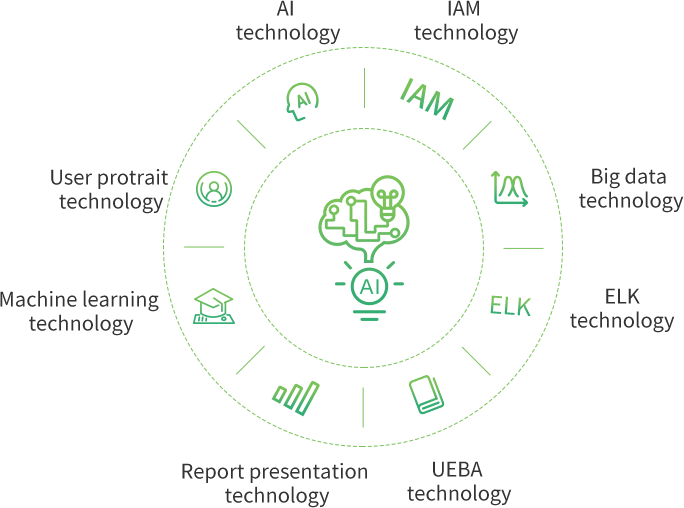
Application Scenarios
-
Intelligent Login Risk Detection
Automatically assess account login risk during authentication and triggers appropriate security actions—such as blocking, step-up authentication, or alert notifications—based on real-time risk analysis. -

Digital Identity Risk Dashboard
Provide organizations with an at-a-glance view of IAM risk posture and trends, helping drive informed information security strategies and reinforce system protection. -

User Behavior Analysis
Track and visualize user activity to build comprehensive user profiles and detect anomalous patterns.
Advantages
-
Adaptive AI risk identification powered by machine learning models with 20+ built-in expert rules
-
Flexible authentication orchestration for intelligent scenario-based authentication
-
Centralized configuration to support diverse application authentication needs
-
Single unified API integration for seamless access to all platform authentication methods
-
Robust security policies and full-stack session lifecycle management
-
Strong authentication eliminates weak passwords and the risk of credential leakage
-
Device fingerprinting and trusted device recognition with unique device ID authentication
-
Omnichannel capabilities—cross-channel, push, and passwordless authentication—enabling secure, mobile-centric authentication across all your channels