Bamboocloud Intelligent Authentication
helps your enterprise to easily cope with the following challenges
-
Complex access environments
 How to secure access to sensitive data when users connect from various locations, networks, and devices?
How to secure access to sensitive data when users connect from various locations, networks, and devices? -
Leveraging AI to its full potential
 How can your organization harness biometric authentication for real-world business scenarios?
How can your organization harness biometric authentication for real-world business scenarios? -
Evolving Information security threats
 With rapid advancements in big data and AI technologies, information security faces unprecedented challenges as hackers increasingly exploit AI for more sophisticated attacks.
With rapid advancements in big data and AI technologies, information security faces unprecedented challenges as hackers increasingly exploit AI for more sophisticated attacks. -
Increasing identity fraud
 How to effectively prevent identity fraud and account takeover?
How to effectively prevent identity fraud and account takeover? -
Abnormal user behaviors
 How to detect anomalous user behavior when accessing internal applications, data, or services?
How to detect anomalous user behavior when accessing internal applications, data, or services? -
Balancing security and user experience
 How to ensure frictionless authentication for users in various scenarios—without compromising security?
How to ensure frictionless authentication for users in various scenarios—without compromising security?
What is AI identity authentication?
Your customers expect seamless access to personalized services, while your organization must protect assets and customer data from emerging fraud and cyber threats. Modern access management solutions like multi-factor authentication (MFA) are replacing traditional passwords to enhance security. However, MFA often leads to inconsistent user experiences, and newer capabilities such as behavioral biometrics, fraud detection, and risk management are frequently siloed.
You need a simple, secure, and future-ready access orchestration solution that unifies identities, applications, and services at the core of your business strategy. By adopting a zero trust and continuous adaptive risk and trust assessment (CARTA) framework, you can strike the right balance between robust security and user choice—delivering a safer, more meaningful experience for every user, across all digital touchpoints, anytime, anywhere.
Overview
Solution Overview
Our authentication solution is designed with scalability in mind, supporting a variety of authentication methods and combinations for web, mobile, desktop, and more. This unified platform offers advanced configuration of authentication engines—including biometric, non-biometric, and social logins—to deliver comprehensive and diversified identity verification across all your business channels. Flexible authentication orchestration allows for tailored combinations based on business needs, significantly enhancing security posture and meeting the evolving demands of fast-growing organizations.
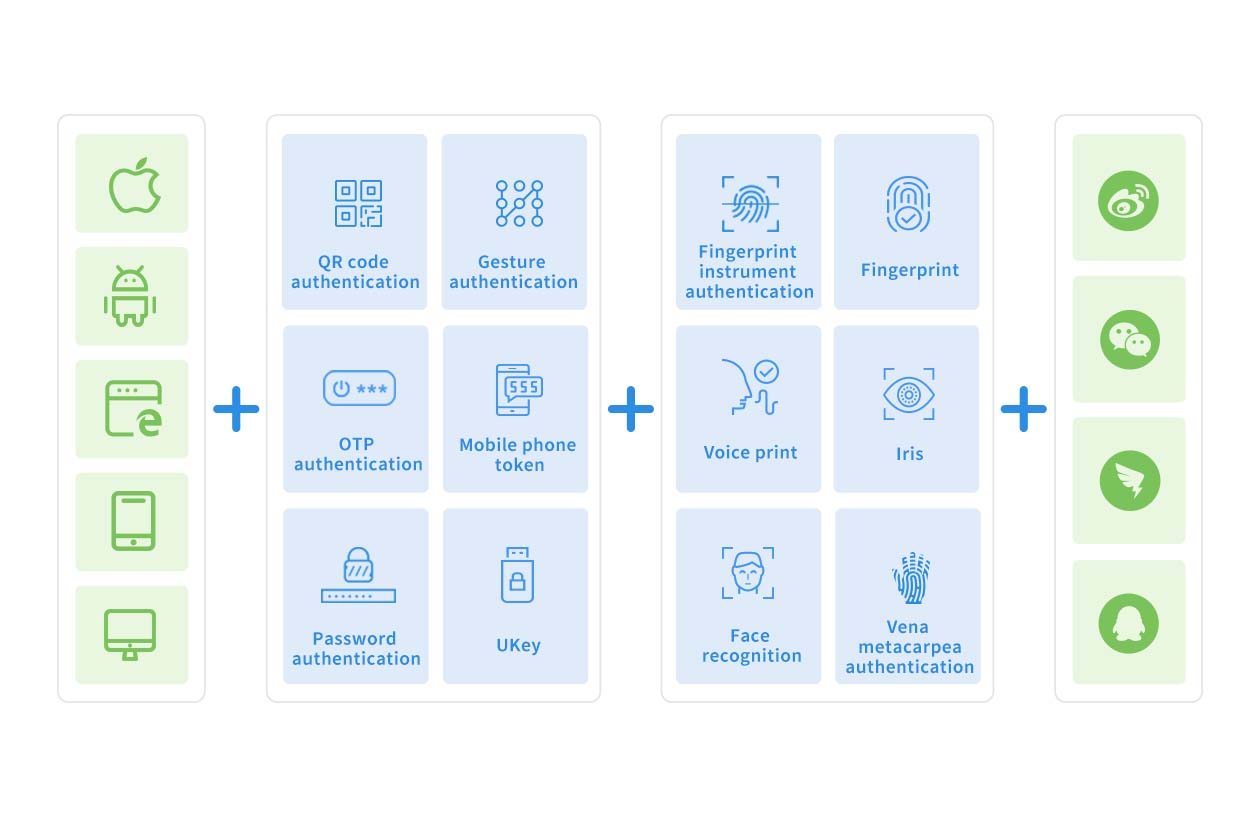
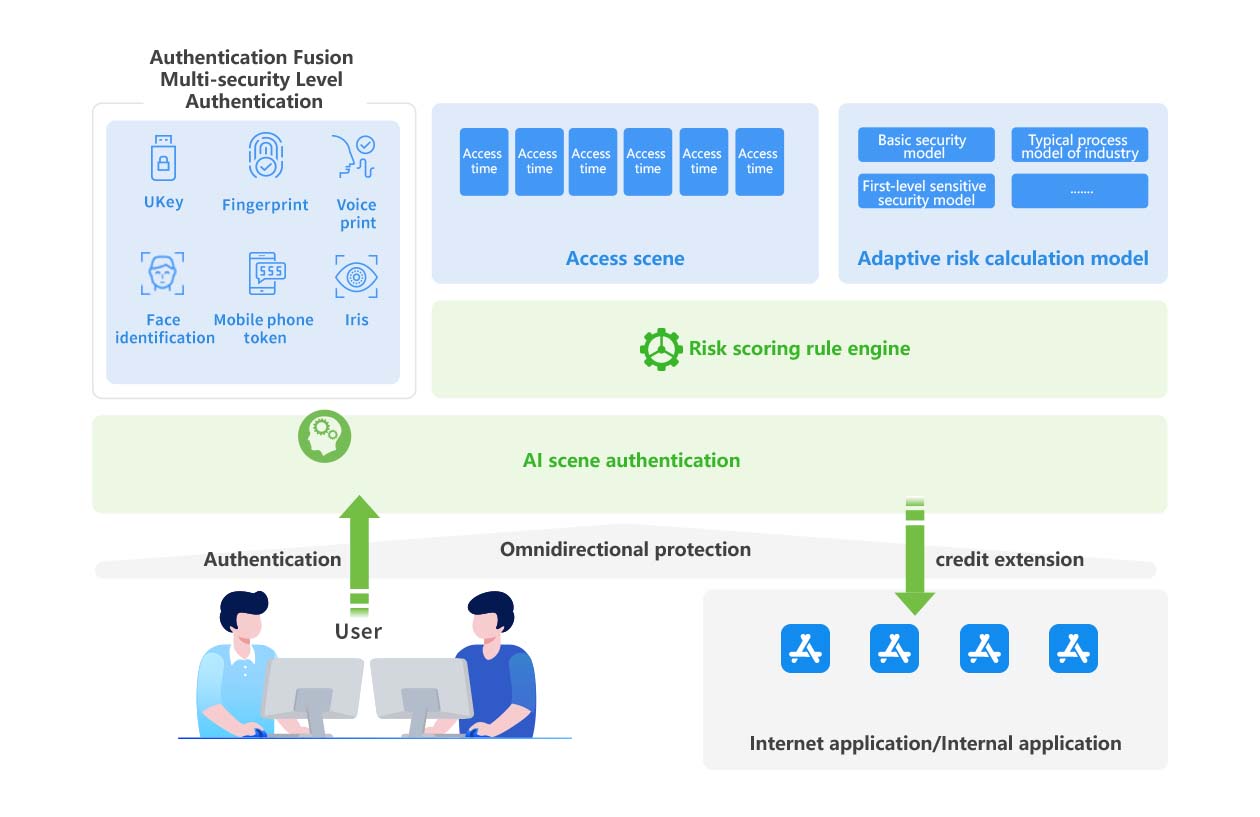
Solution Architecture
Bamboocloud integrates authentication with an intelligent risk engine, performing in-depth analysis of access metadata—such as access time, location, usage patterns, accounts, relationships, and behaviors. The system intelligently adapts authentication requirements based on context, delivering holistic protection for users, applications, and authentication processes to strengthen your security posture.
Rapid Integration

Application Scenarios
-

Prevent Security Risks
Proactively identify and block identity fraud to safeguard business operations and minimize losses. -

Improve Operational Efficiency
AI-driven authentication streamlines user authentication, eliminating the inefficiency of managing multiple disparate authentication tools. -
Enhance User Experience
Real-time, adaptive authentication ensures a seamless user journey—improving engagement and user behavior.
Advantages
-
Integrated authentication framework for one-click authentication enablement
-
Flexible authentication orchestration for intelligent scenario-based authentication
-
Centralized configuration to support diverse application authentication needs
-
Single unified API integration for seamless access to all platform authentication methods
-
Robust security policies and full-stack session lifecycle management
-
Strong authentication eliminates weak passwords and the risk of credential leakage
-
Device fingerprinting and trusted device recognition with unique device ID authentication
-
Omnichannel capabilities—cross-channel, push, and passwordless authentication—enabling secure, mobile-centric authentication across all your channels

