-

Identity Silos
Disconnected identity data across applications makes it difficult to link real user identities, lacks unified, real-time, and effective oversight, and exposes your organization to security risks.
-

Complex User Ecosystem
Beyond internal employees, contractors, vendors, partners, and temporary staff all require centralized governance under your identity management strategy. -

Challenging Application Integration
Different integration approaches across business platforms mean longer deployment cycles and increased complexity for identity governance.
Introduction
BIMBIM is an enterprise-grade platform that unifies identity across all systems. By leveraging digital identity as the core, BIM breaks down information silos and automates account and permission management throughout the entire user lifecycle. The platform delivers a standardized, secure connection for diverse applications, providing your organization with an authoritative master data center and a consolidated, organization-wide view of users and their permissions.
Each user is assigned a unique master account that links all related application accounts. Users can manage their profile, view permissions, and request new accounts or permissions directly on the platform. Upon workflow approval, accounts and permissions are automatically provisioned.
Featutes
BIM-
Centralized Identity Data Storage
Provide enterprise-class directory services, cleansing and mapping all user identity and application account data against unified standards.
-
User Lifecycle Management
Centrally manage user onboarding, changes, access grants, activation, suspension, and removal, with real-time, automatic synchronization across all applications. -
Identity Synchronization
Integrate with multiple identity data sources such as HR, AD, MDM, etc., for automated identity synchronization. Offer an extensive connector library for rapid, code-free integration with leading enterprise software, supporting various integration models. -
Account Discovery & Risk Identification
Regularly audit all accounts within integrated applications to identify and alert on dormant, orphan, and duplicate accounts, mitigating access risks. -
Workflow Automation
Built-in workflow engine with a rich set of process design and development tools for customizable automation. -
Organizational Management Policies
Support multi-dimensional, virtual, and custom organizational structures, enabling hierarchical, delegated management models for headquarters and branch units.
Application Scenarios
BIM-
01
Organization and User Management
Manage the main organization and user of the enterprise, maintain user ID, password, name, phone, email and other basic attributes. Manage the organization to which the user organizations, user positions and other attributes related to account permissions.
-
02
Application Organization and Account Management
Manage the organization and account data in the target application system.
-
03
Application Resource Management
Manage the target application resources of the access platform, such as application roles, application and group data.
-
04
User Self-Service
Users apply for master accounts, application accounts or application permissions independently through self-service. Permissions are automatically obtained after workflow approval. Users can also maintain personal information, view their own permissions and access tracks, change passwords, and self-recovery of forgotten passwords.
-
05
Workflow Management
It has a feature-rich workflow engine with built-in secondary and tertiary approval processes, and also supports customized workflows. The workflow works on the main user and organization, application account, application permissions and other objects.
-
06
Audit and Reporting Management
Provide organizational data statistics. Provide user data statistics by organization and type, etc. Provide application account statistics reports, including orphan accounts in the application that cannot be associated to the main account, and private violation accounts in the application, etc.
ARCHITECTURE
BIMAt the core of the BIM platform is the Identity Management Engine. The Provisioning Engine synchronizes changes to organizations and accounts in real-time across all connected systems. The Synchronization Engine ingests data from upstream sources or reverse-synchronizes from applications for integrity checks. User requests and approvals are managed by the Workflow Engine, while the Reporting Engine powers both standard and custom reports. Scheduled tasks are handled by the Job Scheduler.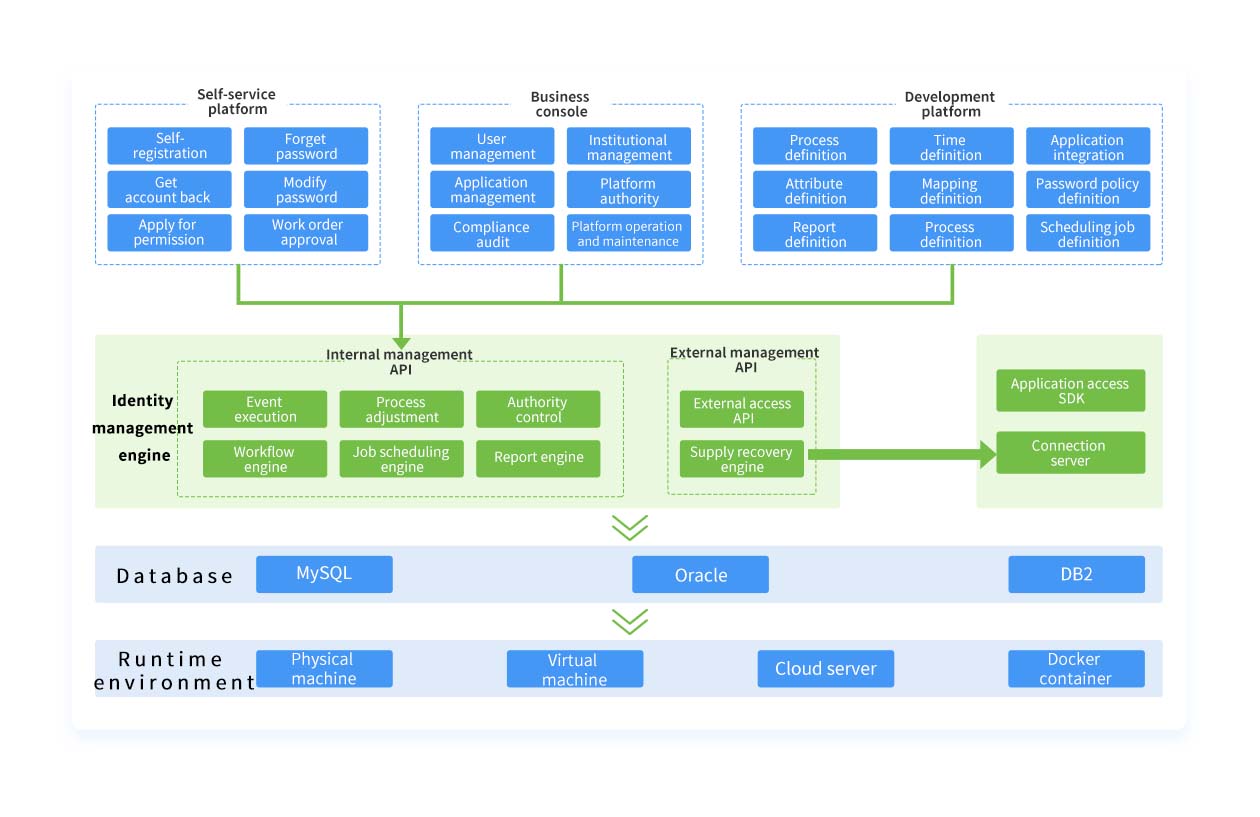
Advantages
BIM-
Full Lifecycle Automation
Automate the user lifecycle management across all integrated systems, enabling one-click onboarding, changes, and synchronization. Streamline all identity processes for maximum operational efficiency.
-
Coverage for All User Types
Centralize management of all user profiles within your enterprise. Easily extend to new user types and tailor management policies to evolving business needs.
-
Rapid Business Adaptation
Leverage advanced policy configuration and workflow design capabilities for quick alignment with your organizational, user, application, and access control requirements.