Bamboocloud Unified Identity Management
helps your organization easily handle the following challenges
-
Increasing number of users and applications
 As digital transformation accelerates, organizations face a growing number of users and diverse applications.
As digital transformation accelerates, organizations face a growing number of users and diverse applications. -
Disconnected account management processes
 Each application manages accounts independently, leading to inconsistent user provisioning and administration.
Each application manages accounts independently, leading to inconsistent user provisioning and administration. -
Lengthy onboarding process
 It takes 3-5 business days to activate accounts for new employees and grant them access and permissions, severely impacting productivity.
It takes 3-5 business days to activate accounts for new employees and grant them access and permissions, severely impacting productivity. -
Inconsistent password policies
 Applications enforce varying password complexity rules, with some lacking password requirements entirely.
Applications enforce varying password complexity rules, with some lacking password requirements entirely. -
Resource waste
 When a new business system is built, if no suitable system is found for reuse, a new user management system has to be built, resulting in a waste of IT resources due to repeated construction.
When a new business system is built, if no suitable system is found for reuse, a new user management system has to be built, resulting in a waste of IT resources due to repeated construction. -
Lack of unified management standards
 No consistent governance framework exists for account management and application integration across the organization.
No consistent governance framework exists for account management and application integration across the organization.
What is unified identity management?
Unified identity management extends secure identity and permission management to all user types and applications—including internal systems, mobile apps, and SaaS tools—without compromising security. By unifying identity governance, it breaks down data silos, streamlines compliance and risk management, and supports automated user onboarding and offboarding. This automated approach greatly boosts efficiency, eliminates manual errors, and strengthens overall security.
Overview
Solution Overview
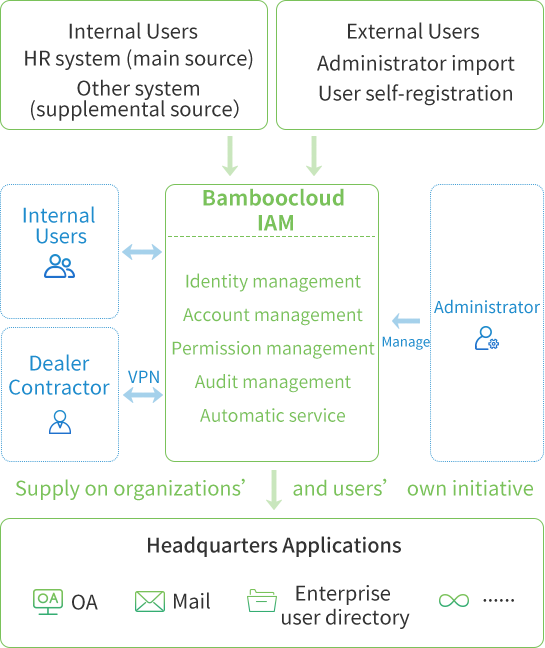
Solution Architecture
Bamboocloud IAM seamlessly integrates authoritative organizational and user data from upstream HR systems. Administrators can also import data or enable user self-registration to establish a unified source of organizational and user master data. Based on organizational structure, department, and roles, IAM automatically assigns application accounts and permissions to users, synchronizing these in real time across OA, email, and user directories. With Bamboocloud IAM, achieve automated account management and streamlined identity provisioning across your applications.
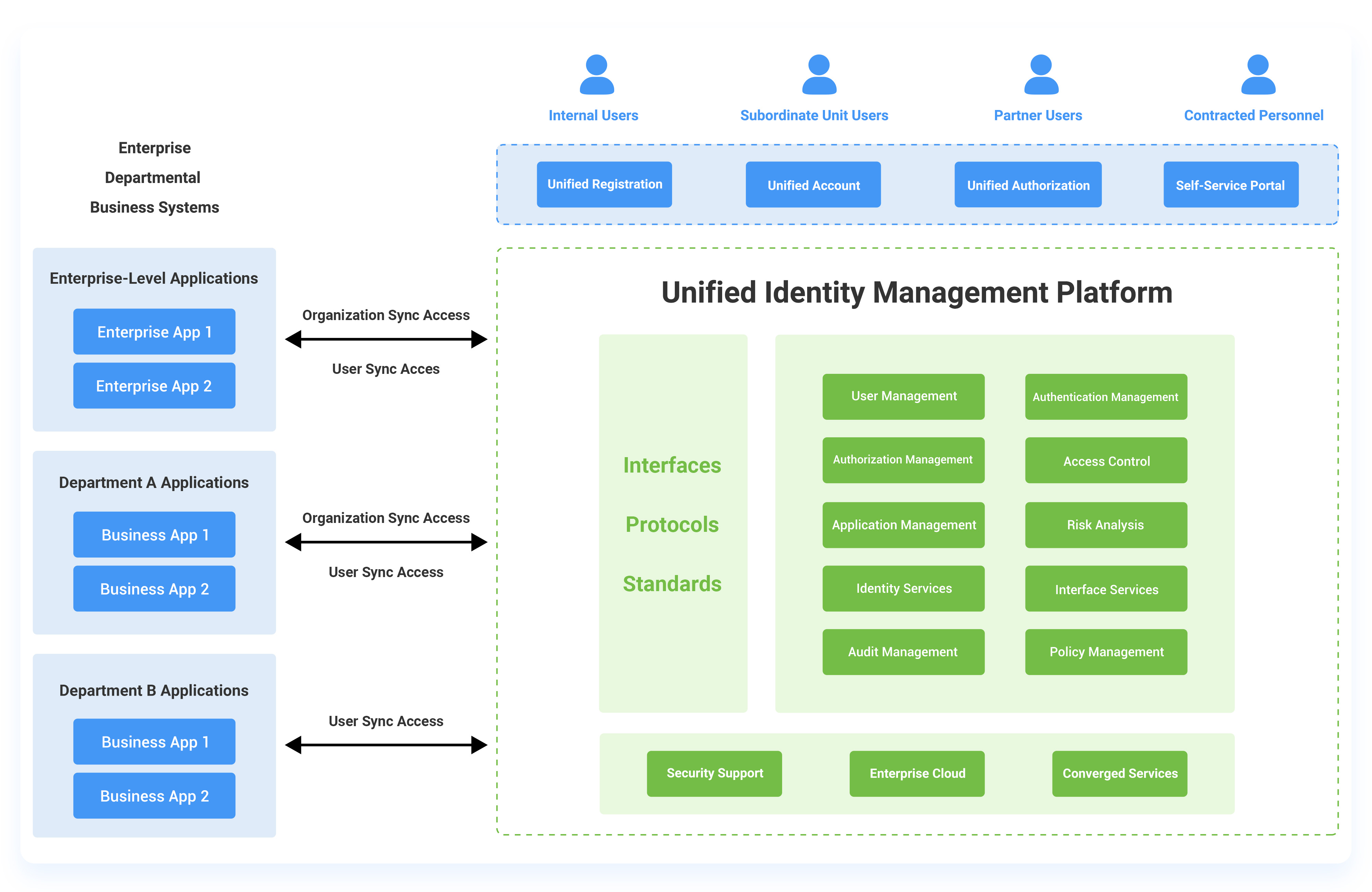
Rapid Integration
Seamlessly integrate with target applications through open, standardized identity interfaces.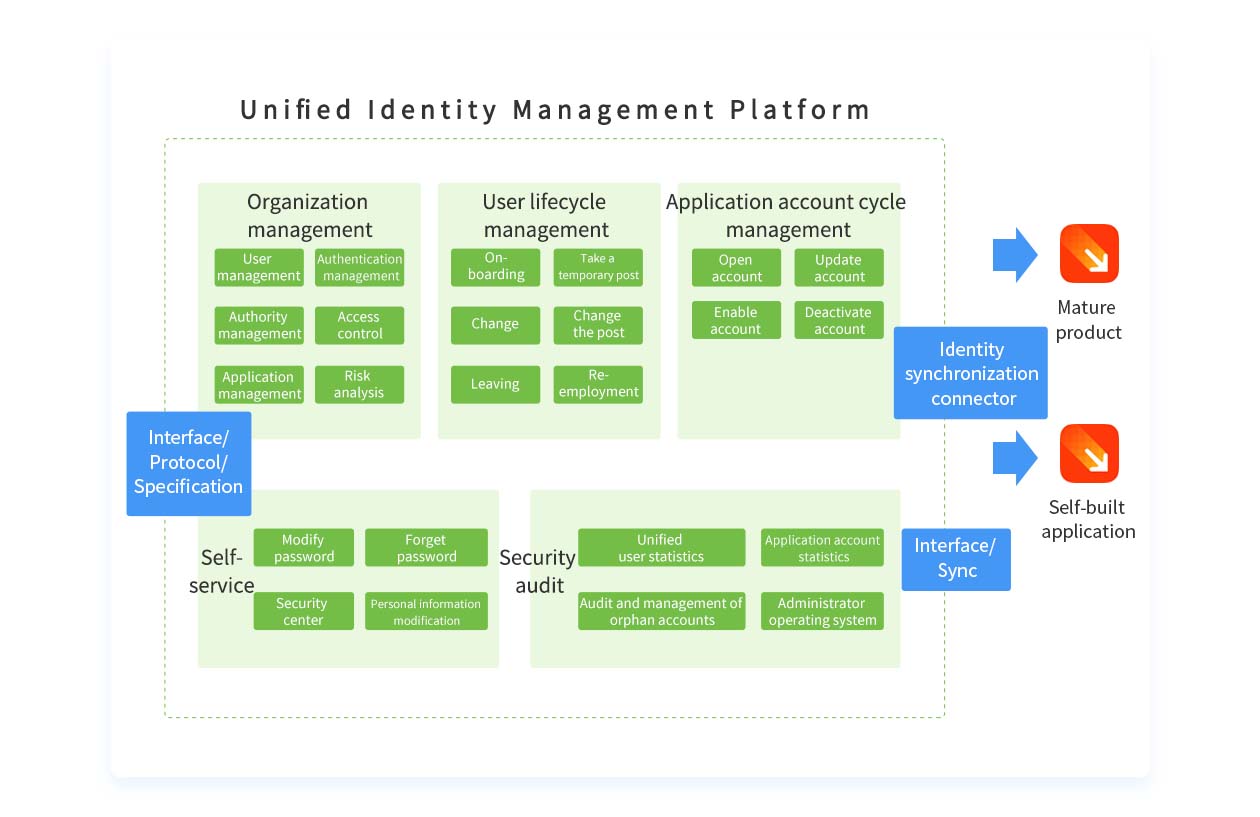
Application Scenarios
-

Centralized Identity Data
Unify user, organizational, and permissions data with IAM as the single source of truth. -

Seamless Identity Lifecycle & Automated Account Management
Automatically provision application accounts and permissions by syncing authoritative user and organization data from upstream HR systems. -
Unified Identity View
Break down silos and access a comprehensive, consolidated view of all identities.
Advantages
-
Establish a single data source for organizational and user data
-
Automate account synchronization—seamless creation, update, activation, deactivation, and deletion of application accounts
-
Centralize management of all user types in one unified platform
-
Automate the full application account lifecycle management
-
Detect high-risk accounts, including duplicate and orphan accounts, across applications
-
Ensure identity data compliance with comprehensive auditing, providing user statistics, account analytics, and compliance reports
-
Unified password policies
Unified management workflowsUnified access integration standards
-
Support Docker deployment
Enable microservices architecture
Ready for cloud deployment