Bamboocloud Solutions
-

Background
In today’s fiercely competitive market, manufacturing enterprises must continuously innovate their technologies and systems to stay ahead. With urgent business transformation needs, manufacturers are driving toward flexible, automated, intelligent, and efficient production. -

Value
In the age of digital transformation, where technology and industry converge, industrial internet is rapidly emerging as a new growth driver. Smart manufacturing requires deep integration of industrial and information technologies, making enterprise information security and risk management more critical than ever. At its core, the industrial internet enables seamless collaboration between people and devices. Identity is now the new perimeter—essential for secure, trustworthy interactions between all key elements. -
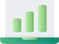
Solution
Bamboocloud delivers end-to-end industrial internet security through its intelligent identity management platform. We enable enterprises to automate the full lifecycle management of digital identities, establish a risk prevention framework that combines adaptive authentication and dynamic risk engines, and empower faster, more agile responses to business innovation.
-

Customer Cases
Leading manufacturers—Haier, Bull Group, Foton Cummins, and Weichai—partner with BambooCloud to build intelligent identity security platforms that break down data silos, centralize identity management, and deliver secure foundations for smart manufacturing.
Key Challenges in the Manufacturing Industry
-

No Identity Lifecycle Management
01/Onboarding, offboarding, transfers, and rehires for internal, external, and overseas staff are managed manually by system admins, creating unnecessary risks.
-

Fragmented and Rigid Authentication
02/Most systems rely solely on static passwords with no unified authentication policies or secure single sign-on capabilities in place. -
No Centralized Management Standards
03/1. Accounts are managed separately across different applications and business units, resulting in inconsistent naming conventions and password policies.
2. Identity data and organizational structures are siloed within systems, leading to potential data inconsistencies.
-
Lack of Unified Audit Logging
04/No centralized user view, making it difficult to visualize, analyze, and review user access and management activities across the organization.
How IAM Solves These Chellenges

Bamboocloud IAM provides user management, authentication management, access management, and auditing. It synchronizes authoritative user data from the central HR system, proactively pushes and pulls user data with downstream systems, and integrates via SAML for federated authentication with local and branch IAM platforms. The OAuth protocol is leveraged for SaaS and mobile app integration.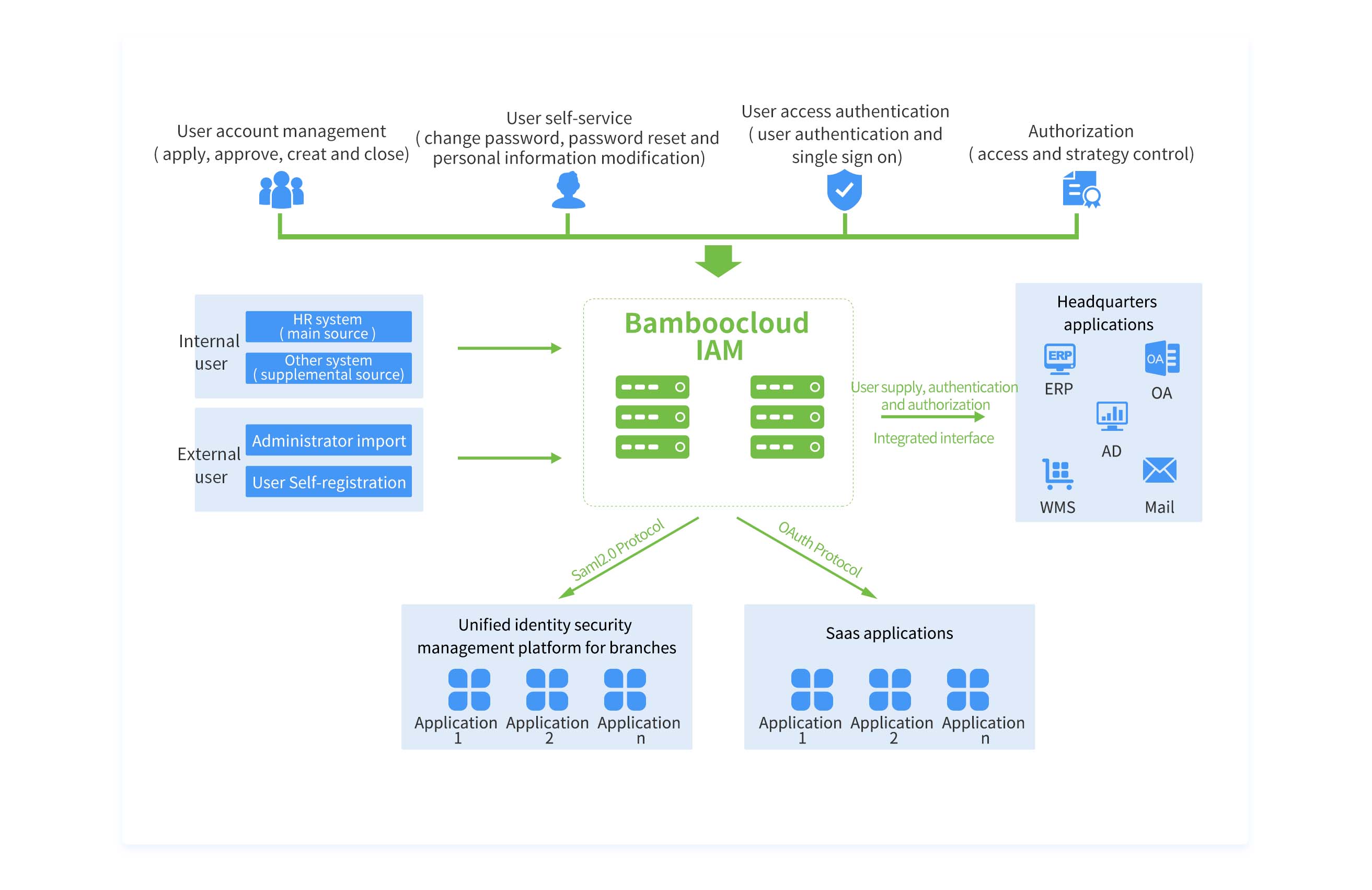
Value
-
Enhance Information Asset Security
1. End-to-end user identity lifecycle management prevents manual data leaks and the creation of dormant accounts.
2. Robust, compliant access management ensures minimal, appropriate permission assignment.
3. Real-name verification and other authentication methods prevent identity fraud and misuse.
-
Strengthen Access Control for Core Systems
Granular, multi-level access authorization and approval minimize the risk of permission abuse, while enabling real-time auditing and traceability.
-
Bolster Core System Security
Multi-factor authentication—including facial, fingerprint, and voice recognition—enhances secure access. UKey integration secures Windows logins. Stronger authentication protects your most critical business data. -
Comprehensive Audit Trails
Every key user action—login, logout, add, edit, delete critical data—is fully logged, enabling comprehensive data statistics, auditing, analysis, and reporting.
Integrated Applications
Bamboocloud has integrated with numerous applications in the manufacturing industry, including SAP, PTC, Windchill, and warehouse management systems, with dozens of pre-built connectors for rapid application integration.