-

Limited Risk Detection
Most organizations can only respond after a security incident occurs—by then, significant and irreversible damage may already have been done. Proactive risk identification and early warning capabilities are often lacking. -

Insufficient Real-time Controls
When a security incident occurs, It could be difficult to pinpoint the source and responsible party. Immediate controls to stop ongoing threats are typically unavailable. -

Difficult Post-Incident Investigation
Thorough investigation of security incidents—especially those impacting multiple areas—is challenging due to fragmented data, making it hard to reconstruct event chains. Response and remediation are often slow and inefficient.
Introduction
RDSThe risk engine is an advanced enhancement to our unified authentication service, acting as its “intelligent brain” for risk analysis. By implementing dynamic risk blocking mechanisms, it delivers real-time alerts on potential access control risks, enabling proactive prevention. Pre-configured risk management rules allow the engine to calculate risk scores for every access attempt, controlling user access based on metadata such as time, location, behavior patterns, account, relationships, actions, and permissions.
This context-aware risk management approach continuously learns user login habits and behaviors, using AI-driven modeling to proactively detect anomalies. By collecting and cleansing access metadata, the system provides comprehensive, real-time evaluation of user actions and immediately blocks suspicious activity or fraud risks to safeguard access security.
Featutes
RDS-
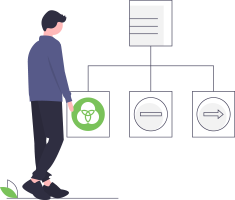
Big Data Platform
Built on a robust data analytics foundation—utilizing Hadoop, Spark, Streaming, ELK, ETL, and more—the risk engine aggregates massive data sets from all points within your IAM ecosystem, supporting the creation and ongoing optimization of risk models.
-
Flexible Data Collection
Support multiple real-time and batch data acquisition methods, with adaptable connectors for diverse data sources. Integrated data collection monitoring ensures reliable and scalable data ingestion. -
Intelligent Risk Analysis Models
Leveraging advanced AI techniques, the risk engine conducts deep analysis of multi-dimensional data, continuously training and refining risk models for more accurate and reliable risk detection over time. -
Adaptive Access Control
Integrate with BAM for real-time behavioral risk assessment. Automatically apply dynamic security measures—such as step-up authentication or access blocking—when risks are detected, while streamlining access for legitimate users to balance security and user experience. -
Extensible Risk Policy Library
In addition to a set of out-of-the-box, configurable risk policies, the platform allows customized rules and models tailored to your unique business requirements and scenarios. -
Risk Scoring Service
Risk detection capabilities are delivered via standard APIs and SDKs, empowering external applications, endpoints, and devices to leverage advanced risk assessment and enforcement with minimal integration effort.
Application Scenarios
RDS-
01
Risk Monitoring Dashboard
Get a comprehensive digital dashboard for multi-dimensional visualization of risk data across your entire environment. -
02
Risk Detection Across All Scenarios
Detect and assess risks across browser/server (B/S), client/server (C/S), mobile, desktop, and device login, authentication, and business transactions. -
03
Pre-Built Risk Models
The platform includes standard risk models and rules for scenarios such as remote login, untrusted devices, unusual IP addresses, and atypical user behavior, covering common security concerns. -
04
Multi-Dimensional Risk Analysis
Correlate data from devices, locations, time, resources, authentication events, behavior, environment, and permissions for holistic risk evaluation. -
05
UEBA Insights
User and Entity Behavior Analytics (UEBA) visualizations provide statistics on access patterns, geographic distribution, device types, authentication preferences, failed login reasons, usage rankings, active users, and risk trends, enabling informed security decisions.
-
06
Risk Audit
Visualizable audit trail for risk events: easily track the timeline, location, involved account details, handling process, risk confirmation, and remediation for closed-loop incident investigation and compliance.
Architecture
RDSDriven by deep learning, the platform performs risk computation on every user access event with comprehensive metadata analysis (time, location, account, relationships, activity, and permissions). It continuously models user behavior and enables real-time data visualization and unified analytics with industry-standard, open-source technologies.
Advantages
RDS-
Advanced Risk Data Aggregation
Utilize the Elastic Stack (Beats, Logstash, Elasticsearch) to collect and store activity logs. Natively integrate log collection from our unified authentication platform and risk-based authentication solutions, with the flexibility to ingest logs from additional business systems as required.
-
Context-Aware Risk Scoring
Deliver specialized, scenario-based risk analysis services, powering intelligent multi-factor authentication for unified identity services or providing standalone anomaly detection for independent applications.
-
Flexible Risk Rule Engine
Offer a customizable, visual policy builder for risk rules—enable dynamic risk strategies tailored to various contexts, with each scenario leveraging distinct policies as needed for targeted protection.
-
Channel & Scenario Management
Associate business applications and processes with risk rules, providing risk assessment services per scenario. Easily add, remove, enable, disable, edit, query, or cross-link application channels and associated risk strategies for streamlined administration.