Bamboocloud Zero Trust
helps your enterprise to easily cope with the following challenges
-
Weak application protection
 Applications are exposed within the enterprise network, making it easy for anyone on the network to access application hosts. This leaves critical systems vulnerable to malware and a variety of attacks.
Applications are exposed within the enterprise network, making it easy for anyone on the network to access application hosts. This leaves critical systems vulnerable to malware and a variety of attacks. -
Traditional security Is no longer enough
 Legacy security architectures rely on “defense in depth” and perimeter security—approaches that struggle to keep pace with rapid business growth and change.
Legacy security architectures rely on “defense in depth” and perimeter security—approaches that struggle to keep pace with rapid business growth and change. -
Lack of continuous security enforcement
 Without ongoing identity authentication and dynamic authorization, organizations can’t adapt access policies in real time or respond swiftly to new threats.
Without ongoing identity authentication and dynamic authorization, organizations can’t adapt access policies in real time or respond swiftly to new threats. -
Ineffective authentication mechanisms
 Network isolation separates network and application authentication. Once connected, unprotected application traffic can freely flow into the data center, putting sensitive data and resources at risk.
Network isolation separates network and application authentication. Once connected, unprotected application traffic can freely flow into the data center, putting sensitive data and resources at risk. -
Infrastructure limitations
 How to elevate the security posture and improve efficiency without costly changes to the existing environment?
How to elevate the security posture and improve efficiency without costly changes to the existing environment? -
Accelerate security transformation
 Organizations seek to simplify network architecture and reduce operational risk, while meeting compliance requirements and enhancing the experience for customers and employees.
Organizations seek to simplify network architecture and reduce operational risk, while meeting compliance requirements and enhancing the experience for customers and employees.
What is Zero Trust
Bamboocloud Zero Trust Solution is an identity-centric security platform composed of key modules including: Zero Trust Identity Security Gateway, Data Security Gateway, API Security Gateway, Email Security Gateway, Privileged identity Management Gateway, Zero Trust Security Service Platform, Identity Authentication & Access Control Center, Risk Assessment & Policy Center, and Zero Trust Security Client.
Our approach is built around digital identity as the foundation, permission as the boundary, continuous trust assessment, and dynamic access control. Bamboocloud empowers organizations to secure remote workforces, harden internal networks, manage privileged access, and protect hybrid operations—addressing today’s most complex security challenges with confidence.
Overview
Solution Overview
Bamboocloud Zero Trust delivers an efficient, secure, stable, and user-friendly infrastructure. Built on dynamic IAM and centered on digital identity, the solution delivers robust security for remote, hybrid, branch, and partner access scenarios. The platform authenticates and authorizes trusted users, establishes secure chains of trust, minimizes the attack surface, and dynamically adapts security policies—enabling secure communications across organizational units, regions, and business systems.
Solution Architecture
On the basis of identity, authentication and authorization, we integrate existing security products, provide environment awareness, trusted agent and control services, control access based on the principle of minimizing authority, and guide the security architecture from network-centric to identity-centric. Instead of relying on network location to judge whether access is allowed, we continuously evaluate the security and risk status of devices, systems, users, environment, behaviors and access flows, so as to achieve fine-grained and dynamic security access control.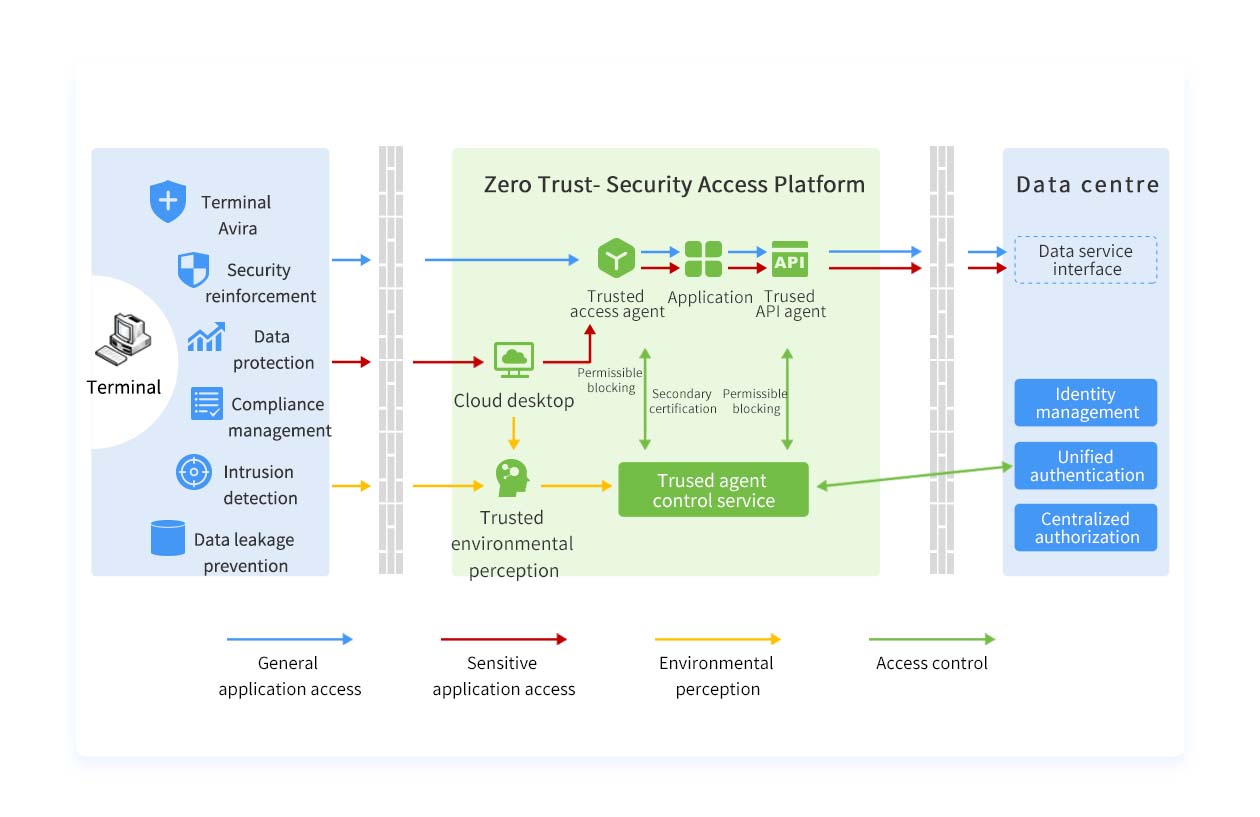
Chain of Trust
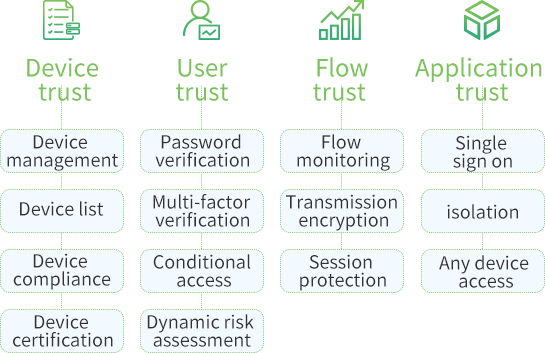
Core Value
-

Dynamic Data Detection and Masking
Inspect all data flows to identify sensitive information. Built-in rules detect and flag data leaks or sensitive data, enabling automated data masking and leakage prevention. -

Minimize Attack Surface & Protect Resources
Conceal real host addresses and domain names, enforce authentication before connection, and encrypt communication channels—eliminating risks from exposed applications. -
Context-Aware Protection
Access is only granted when both device identity and security posture are trusted. If risk is detected, the platform triggers secondary authentication or blocks access based on policy.
Advantages
-
Privileged identity management
-
Defend core business assets exposed to external networks
-
Enhanced protection for critical internal systems
-
Secure access for remote workforce

