Bamboocloud Intelligent Permission Management
helps your enterprise to easily cope with the following challenges
-
Fragmented access request channels
 Multiple request entry points, complex approval flows, and lengthy provisioning cycles.
Multiple request entry points, complex approval flows, and lengthy provisioning cycles. -
Unclear permission definitions
 Technical jargon and unclear terms make permissions difficult to understand.
Technical jargon and unclear terms make permissions difficult to understand. -
No unified permission model
 Diverse permission models across applications hinder standardized reviews and governance.
Diverse permission models across applications hinder standardized reviews and governance. -
No unified development framework
 Repeated development efforts waste valuable resources.
Repeated development efforts waste valuable resources. -
Lack of compliance controls
 Absence of segregation-of-duty rules leads to serious permission misuse.
Absence of segregation-of-duty rules leads to serious permission misuse. -
High volume, low efficiency
 Manual processes and lack of automation slow down approvals and reduce effectiveness.
Manual processes and lack of automation slow down approvals and reduce effectiveness.
What is the intelligent permission management?
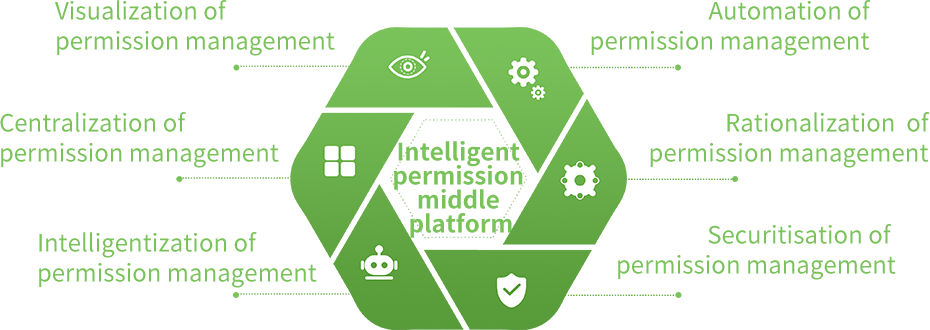
Bamboocloud intelligent permission management platform is a user-centric, intelligent access governance solution designed to tackle the core challenges of permission provisioning, discovery, deprovisioning, and ongoing management. Our platform delivers centralized, automated, standardized, secure, visualized, and intelligent permission management for your entire enterprise, driving rationalization, efficiency, enhanced security, and a superior user experience—while dramatically reducing the costs and complexity of access management and maintenance.
Overview
Solution Overview
Built around centralized permission management, Bamboocloud establishes standardized permission governance across the enterprise. Reduce IT development and operational costs, drive management efficiency, and strengthen compliance.
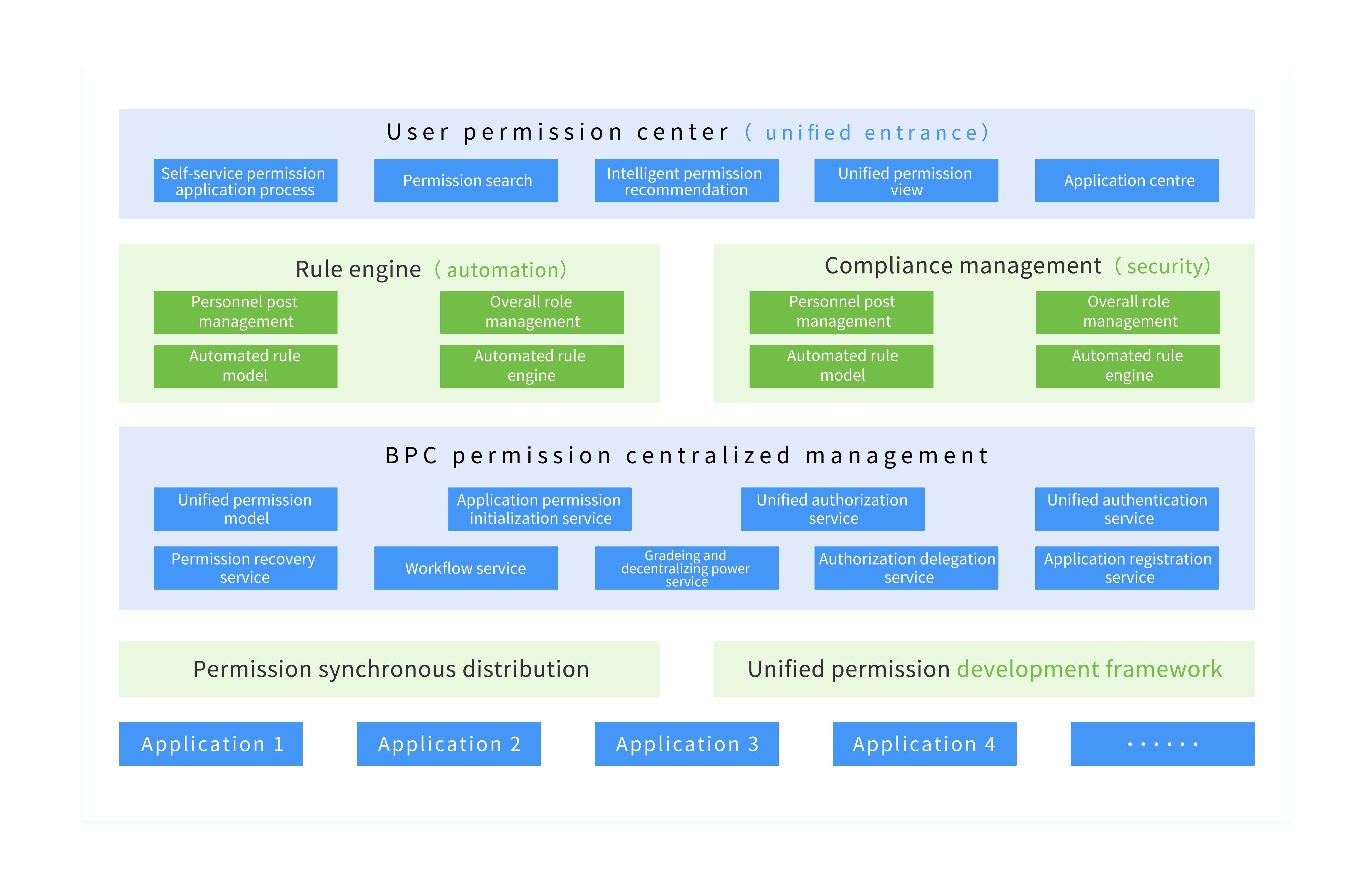
Solution Architecture
The solution architecture adopts a layered design. The top layer is the user permission center, where users can self-service permission requests through a single portal. The solution provides a complete model framework supporting RBAC, ACL, ABAC, TBAC, and custom model s. Core services include: application permission initialization, unified authorization service, unified authentication service, hierarchical decentralization service, and permission delegation service.
Permission Compliance Audit
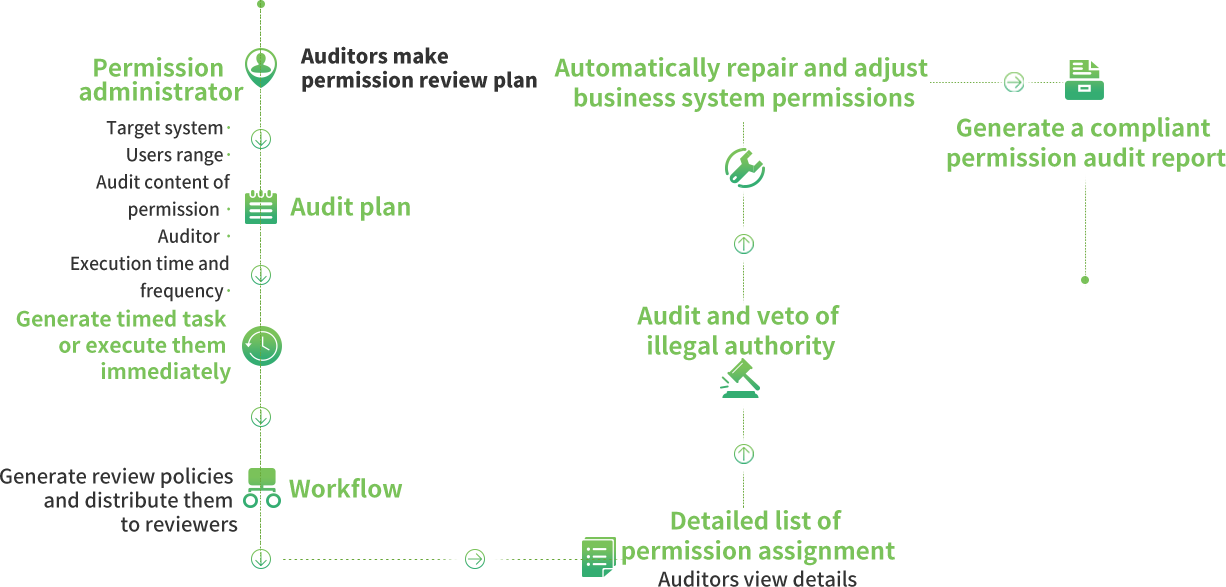
1. Auditors and security personnel establish compliance audit rules through the permission platform, such as the SAP position-role mappings and compliance checks.
2. Non-compliant permission requests can be flagged for exception handling or rejected during approval workflows.
3. The permission platform notifies users of permission results via email and task notifications.
4. Regular review and auditing of permissions and position compliance, including compliance reports.
Application Scenarios
-

Unified Permission Request
Centralized IT operations, automated permission distribution, and elimination of redundant workflows.
-

Intelligent Permission Recommendations
Personalized permission recommendations and permission-to-user matching enhance user experience. -

Automated Role-Based Authorization
Consistent permissions by role for easier search, request, and management.
Advantages
-
Unified permission framework to reduce duplicated development for new applications
-
Centralized permission management facilitates routine compliance audits
-
Automated permission assignment reduces operational workload
-
Single permission request and approval portal boosts user experience and efficiency
-
Rigorous application publishing ensures high quality
-
Centralized application management mitigates risks
-
On-demand permission assignment drives higher productivity
-
Unified audit portal enables end-to-end risk control