-

Inconsistent Access Standards
Disjointed authentication systems across enterprise applications lack a unified, security-compliant standard, leading to inconsistent reliability and potential security gaps.
-

Weak and Limited Authentication Methods
Many applications still rely on static password authentication, increasing risks related to weak passwords, easy breaches, and data leaks. -

Poor User Experience
Users must remember multiple accounts and passwords and log in to various application portals, resulting in low efficiency and high frustration. There is limited access to secure and convenient methods like biometrics and multi-factor authentication.
Introduction
BAMBamboocloud Access Management platform (BAM) unifies authentication and access control across all enterprise applications. Designed for seamless user and system integration, BAM provides consolidated authentication, authorization, and access control—featuring strong identity verification, session auditing, and centralized management in a single solution.
Control access across internal users, administrators, and all business operations. BAM supports multiple authentication methods—username/password, mobile OTP, digital certificates, SMS, and token-based solutions—and is compatible with standards such as SAML and OAuth. Streamline the login process and dramatically reduce authentication time and complexity for end-users.
Featutes
BAM-
Intelligent Risk Control
Built-in risk detection modules proactively identify authentication and access threats in real time, dynamically adjust security levels and access policies, and effectively block unauthorized attempts.
-
One-Time Integration, Automated Enablement
Onboard applications once—any subsequent changes, upgrades, or removals of authentication methods can be managed centrally with zero application modifications and no downtime. -
Rapid Security System Deployment
Quickly establish a unified authentication and access management framework tailored to enterprise requirements and industry standards, delivering consistent, centralized security for all applications. -
Comprehensive Pre-Integrated Authentication Options
Out-of-the-box support for major authentication services—including traditional, biometric, third-party enterprise, and social authentication—plus flexible expansion for new authentication capabilities. -
Fast Application Integration
Seamlessly connect with any application via a range of integration options. Offer pre-built connectors for widely used enterprise software, enabling zero-effort onboarding for commonly used applications.
Application Scenarios
BAM-
01
Unified Access Portal
Provide a single login portal and centralized navigation for all applications. Enable users to access every system with one account, improving both experience and efficiency. -
02
Comprehensive Policy Management
Assign security levels and configure authentication methods per application requirements. Flexibly combine serial or parallel authorization policies across all systems. -
03
Universal Single Sign-On
Deliver seamless SSO—across B/S, C/S, browsers, on-premises and cloud environments, and partner ecosystems. Support SSO after network or VPN access, and from desktop login for true cross-scenario coverage. -
04
Versatile Integration Modes
Support leading authentication standards such as OAuth, SAML, OpenID, CAS, and Radius; integration options including RESTful APIs, SDKs, and interceptors; token modes like JWT, LTPA, AMToken; as well as channel proxy, form autofill, and more.
-
05
Multi-Factor Authentication & Extensibility
Enable multiple authentication modes: passwords, certificates, SMS, biometrics (fingerprint, voice, facial), third-party platforms (AD, DingTalk, WeCom), social logins (WeChat, QQ), and extend as needed.
-
06
Passwordless Login
Leverage biometric authentication such as facial recognition to enable automatic system login at desktops or workstations—no passwords required. System auto-locks upon user departure, balancing seamless access with security.
Architecture
BAMBAM delivers unified authentication and access control for all enterprise applications, quickly establishing secure, resilient access management to minimize risks of unauthorized access and data breaches—all while maximizing usability for end-users.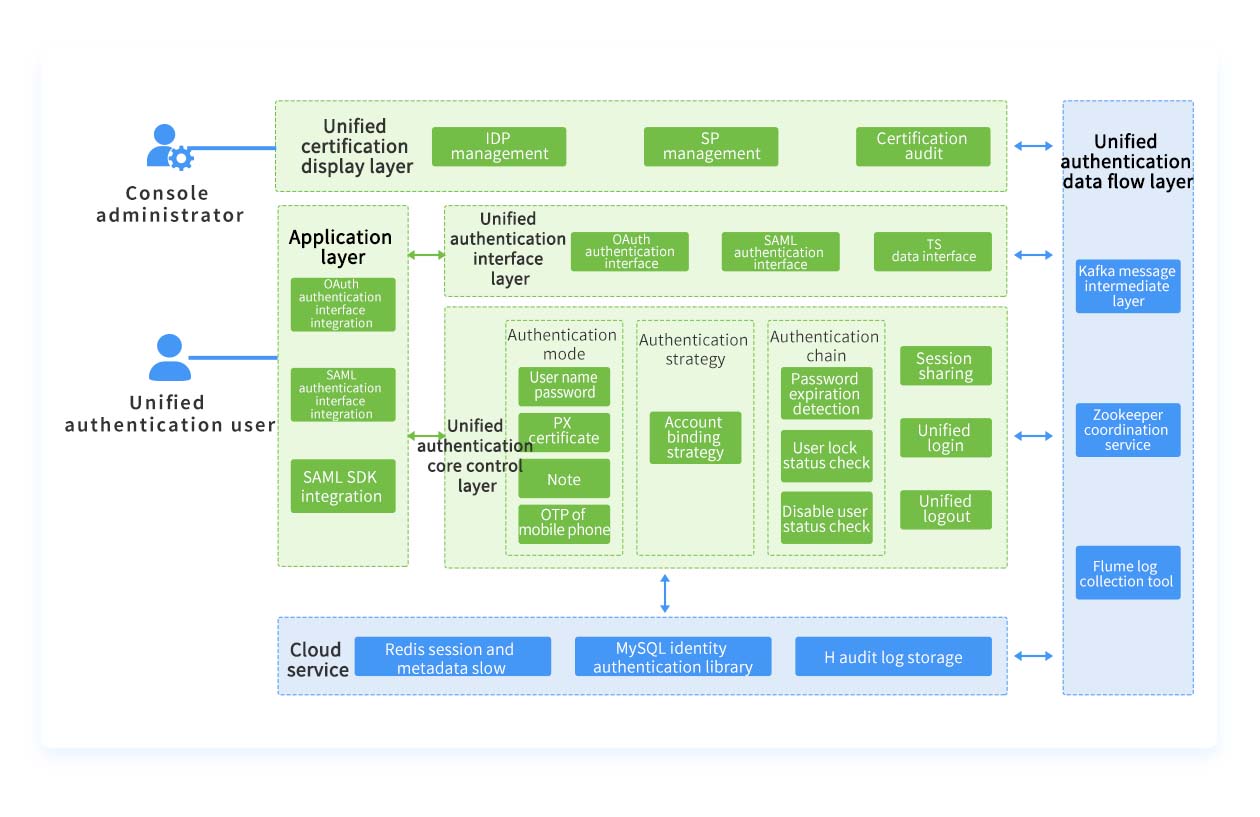
Advantages
BAM-
Seamless Integration
Support SDK and RESTful integration, enabling applications to connect without invasive changes for rapid, low-effort deployment.

-
Openness
Application-oriented architecture simplifies integrations. Multiple options—including RESTful APIs, SDKs, and proxies—make connecting new or existing applications easy and flexible.

-
Extensibility
Custom interfaces support diverse business needs, ensuring system agility and scalability. Centralized session management enables smooth system expansion and stateless operation across all applications.
-
Security
Support granular access control, fine-tuned authorization policies, authentication chaining, and multi-layered interception. Comprehensive system and security auditing provides full visibility into daily operations and incident analysis.