Bamboocloud Solutions
-

Background
The State Council's Guidelines on Accelerating the Construction of a Unified National Online Government Service Platform ([2018] No. 27) call for unified identity authentication and integrated public support. The Digital Government Implementation Plan (2018-2020) ([2018] No. 48) further emphasizes strengthening business application support and promoting standardized identity authentication services. -

Value
Countless incidents show that information leaks often originate internally. For example, data from the Guangdong Provincial Public Security Department’s online immigration services was compromised due to faulty access controls—ordinary users bypassed login and accessed sensitive backend data, resulting in mass data leakage for anyone who had filed an online application. -
Solution
Following the principles of "unified planning, unified standards, unified platform, and unified management," Bamboocloud helps build a trusted digital identity center (IAM platform) that integrates and enhances e-government infrastructure resources, improves the "Internet + Government Services" support system, and enables digital identity interoperability across all user levels through integration with business systems at every tier.
-

Customer Cases
Shenzhen Longgang District Government and Pingshan District Government partner with Bamboocloud to build an intelligent identity security management platform, breaking down departmental barriers, enabling data sharing and collaboration, assisting the government in intelligent decision-making, and delivering precise, citizen-centric public services.
Key Challenges in Government Sector
-
Insufficient Identity Management for Government Users
01/1. Government staff use real identities but manage multiple accounts.
2. Lack of data synchronization with personnel authorities causes isolated identity silos.
3. Identity information updates are delayed and lack authority.
4. System users do not cover all personnel, excluding temporary and contract staff.
-

Public User Identity Security Risks
02/1. No unified security standard—identity management and access controls are inconsistent across systems, leading to redundant work and varying protection levels.
2. Limited support for fast and secure public access via social accounts, fingerprint, or facial recognition.
-
Fragmented Access Management
03/No unified role and permission model; authorization lacks standardization.
-
Lack of Granular Management
04/Insufficient understanding of public needs and inadequate enterprise services fail true citizen-centric governance. Smart government represents the breakthrough for e-government evolution and the natural progression from "administrative" to "service-oriented and intelligent" government.
How IAM Solves These Challenges

Built on Bamboocloud's IAM foundation, our comprehensive unified authentication platform solution includes authentication management, application management, single sign-on, session management, access control, and security auditing. This enhances service quality, reduces user acquisition costs, improves user experience, and helps establish unified authentication management standards, laying a solid foundation for new channels and business development.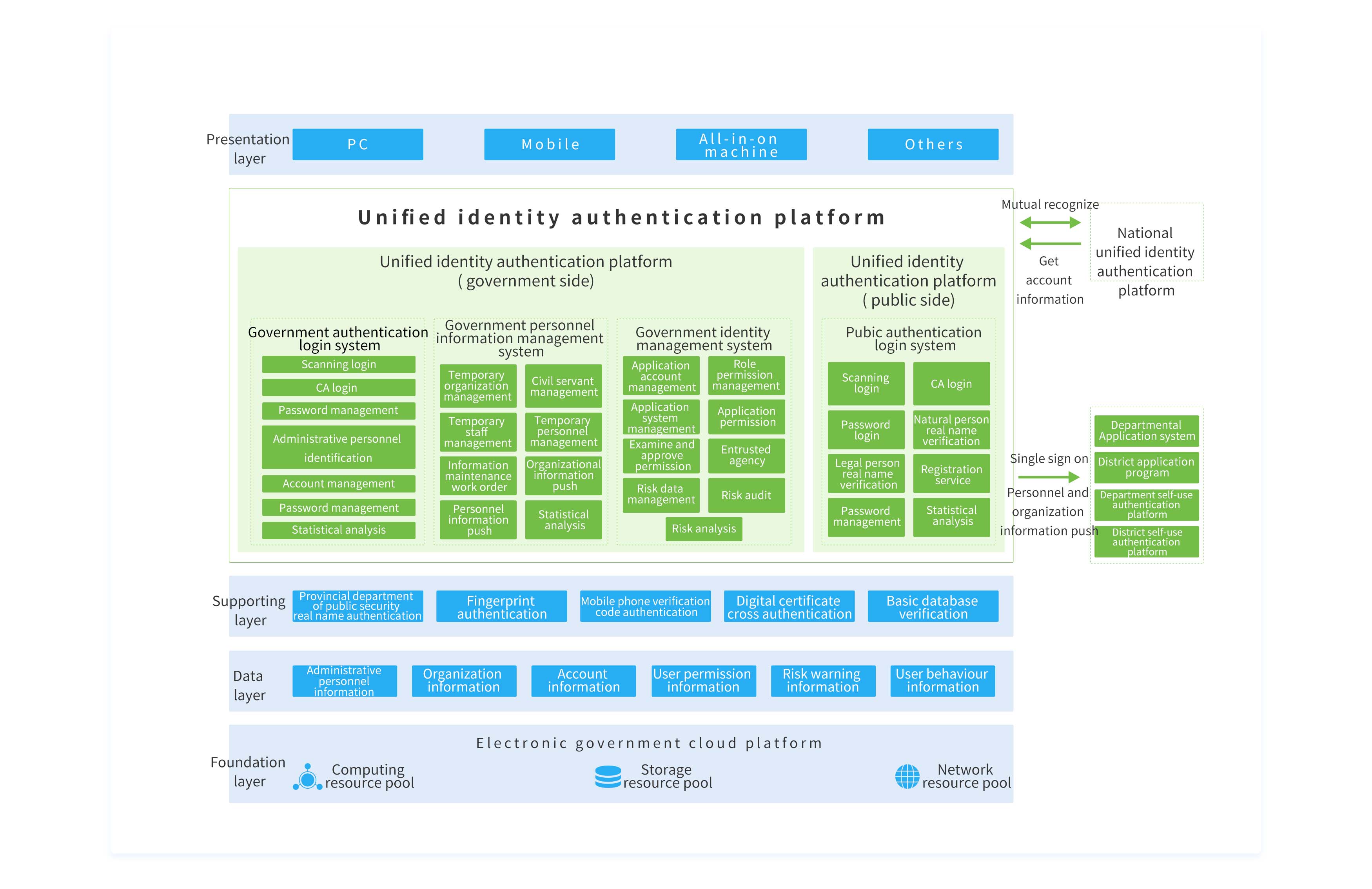
Value
-
Eliminate Identity-Based Security Loopholes
Automate lifecycle management for digital identities across all user types. Control shared account usage by clearly identifying individual users, strengthening security monitoring.
-
Enhance Access Control for Core Systems
Implement granular, hierarchical authorization and approval processes for critical systems. This prevents permission abuse, enables real-time audits, and ensures full traceability.
-
Strengthen Core System Access Security
Leverage advanced biometric authentication—facial, fingerprint, or voice recognition—to safeguard access, and enable UKey locking for Windows environments. Enhance identity verification for critical applications to secure sensitive business data.
-
Comprehensive Audit Trails
Record every critical user action—logins, logouts, data additions, updates, and deletions. Audit logs can be tracked, queried, analyzed, and reported for compliance and governance.
Integrated Applications
Bamboocloud has integrated witha wide range of e-government applications, including management systems, WeChat for government, data exchange platforms, and smart light poles, with dozens of pre-built connectors for rapid application integration.