-

Difficult Permission Provisioning
Users face multiple complex entry points, lengthy approval cycles, and confusing terminology when requesting permissions. Manual authorization processes lead to inefficiencies and slow onboarding. -

Challenging Permission Revocation
When employees change roles, depart, or vendors’ responsibilities shift, administrators must manually remove related permissions from various systems—creating heavy workloads, delayed deprovisioning, and potential security risks. -

Complex Permission Auditing
Inconsistent auditing capabilities across applications make unified, compliant oversight of permission data and processes difficult. There is a lack of effective tools for both in-system and cross-system permission compliance.
Introduction
BPCThe Bamboocloud Intelligent Permission Center (BPC) provides a centralized gateway for unified permission management. Automate assignment and revocation of business and system permissions throughout the entire identity lifecycle. Empower users with self-service permission requests, modification, and revocation, ensuring the right people have the right permission at the right time. Leverage an automated rule engine for semi-automated and rule-based provisioning—across accounts, departments, job roles, and more. Enjoy fine-grained permission managemnent by data classification. BPC enforces compliance policies, supports separation of duties (SoD), automates alerts, approval workflows, and end-to-end reporting for complete governance.
Featutes
BPC-
Standardization
Establish standardized permission models and workflows tailored to enterprise business processes. Normalize permission data and streamline management practices, ensuring consistent governance across all permissions. -
Centralization
Consolidate permission data from all applications into a single repository. Provide unified management interfaces and views, enabling centralized oversight, control, and administration of permissions across diverse systems. -
Compliance
Enforce compliance with robust rules: separation of duties, mutual exclusion, least privilege, and more. Conduct regular permission reviews, risk assessments, automated alerts, event audits, and generate compliance reports for complete audit trails. -
Intelligent Automation
Utilize advanced analytics across identity, organizational, and role attributes for personalized permission recommendations and automated provisioning. Leverage big data insights to drive efficient permission management and informed decision-making. -
Comprehensive Risk Assessment
Deploy SoD engines and access compliance analytics for robust defense against permission abuse and policy violations. Experience 360° closed-loop audit mechanisms. -
Cost Minimization
Leverage an extensible permission model and standardized frameworks to rapidly deploy compliant permission management with minimal overhead. Automate provisioning and deprovisioning to reduce administrative effort and costs.
Application Scenarios
BPC-
01
Unified Permission Visibility
Gain centralized, comprehensive views of user permissions across all systems—in real time. Simplify permission reviews, queries, and administration. -
02
Custom Permission Model
Define application-specific permission models via intuitive interfaces. Map relationships across users, departments, roles, and resources. Built-in support for RBAC, ACL, ABAC, and other leading models.
-
03
Permission Rules Engine
Configure automated, context-aware provisioning and deprovisioning rules based on user role, department, status changes, and more—dramatically improving efficiency and reducing manual risk.
-
04
User Permission Center
Empower users to view, manage, and request their own permissions through a dedicated portal. Intelligent recommendations streamline permission requests, enhancing self-service experiences. -
05
Regular Compliance Review
Define and automate compliance review schedules for ongoing permissions audits within and across applications. Trigger security notifications, enforce closed-loop event resolution, and deliver comprehensive compliance reports. -
06
Unified Permission Framework
Standardize permission management for new applications via SDKs and modular frameworks. Rapidly implement compliant permission features, reducing development and compliance costs.
Architecture
BPC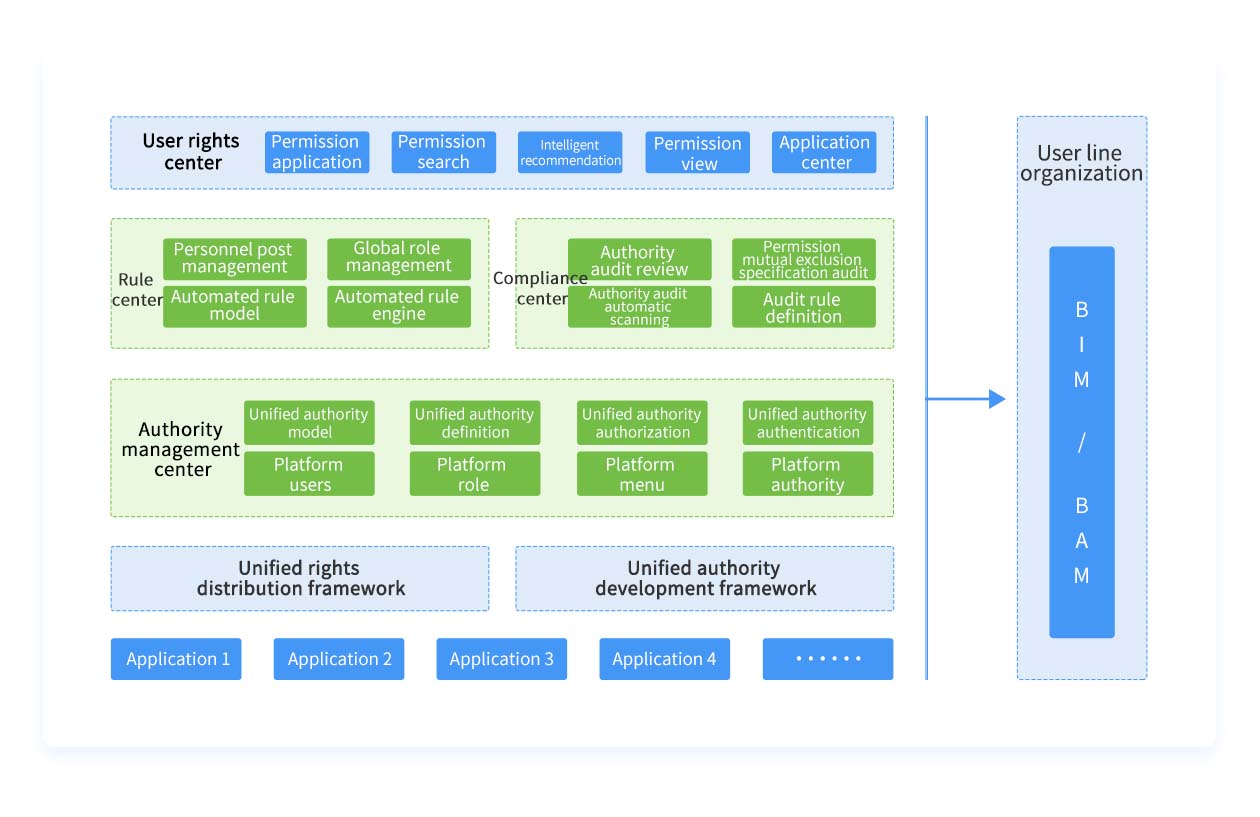
Advantages
BPC-
Centralized Permission Requests
Unified request and approval process enhances efficiency, user experience, and productivity.
-
Enterprise Application Center
1. Rigorous application vetting improves quality.
2. Centralized application management strengthens control and mitigates risk.
3. On-demand, user-driven access boosts business agility.

-
Automated Role-Based Provisioning
Centralize role-permission relationships, automate onboarding/offboarding, and provide real-time, consolidated permission views.

-
Audit & Compliance Management
1. Proactively monitor, alert, and manage permission risks.
2. Enforce compliant, mutually exclusive permissions.
3. Generate periodic compliance audit reports with ease.


