-

Shared Account Risks
Privileged accounts are often shared, increasing the risk of unauthorized access. Many device credentials do not meet security compliance standards. -

Complex Permission Management
It's challenging to assign appropriate device permissions and monitor administrative activity effectively. -

Difficult Centralized Auditing
Tracking and auditing usage across all devices through a single platform is often unmanageable.
Introduction
PIMBy unifying privileged account lifecycle management, centralized authentication, unified authorization, single sign-on (SSO), password synchronization, and activity auditing, PIM enhances both access and operational security. Gain centralized, secure oversight of your critical infrastructure and user activities, including authentication, authorization, and operational actions.
Featutes
PIM-
Centralized Device Management
-
Privileged Account Use Isolation
-
Privileged Account Lifecycle Management
-
Unified Access Authorization
-
Multi-Factor Authentication
-
Centralized Auditing
Application Scenarios
PIM-
01
Single Sign-On to Device Resources
Access all authorized devices after one login. No need for repeated authentication, preserving familiar workflows and supporting a variety of client tools. -
02
Step-Up Authentication for Sensitive Resources
Enforce secondary authentication for access to high-security assets.
-
03
Integrated Approval Workflows
Built-in workflow engine for access and operation approvals. -
04
Dual Control for Critical Operations
Require joint operations for sensitive systems, with one user initiating the action and another providing approval. -
05
Broad Device Compatibility
Support all major operating systems, endpoints, network and security devices, databases, and protocols. -
06
Multi-Dimensional Audit
Capture detailed audit logs and generate corresponding reports and analytics.
Architecture
PIM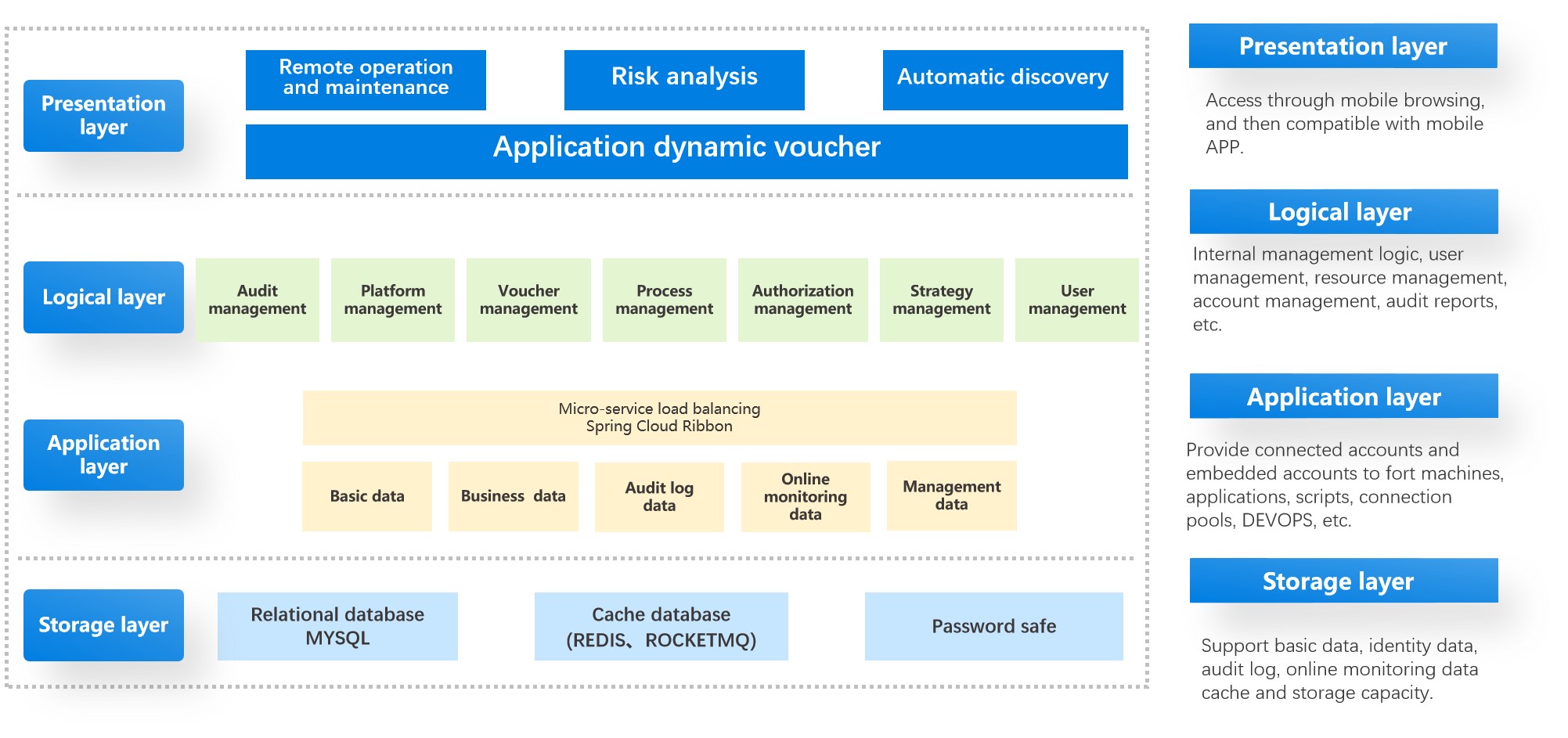
Advantages
PIM-
Full Visibility and Audit Trail for Human and Device Access
Every privileged credential usage is tracked and audited, whether accessed manually or via application, tool, or script. Built-in workflows for password requests and approvals ensure secure credential handling.
-
Extensive Credential and Password Support
Manage all types of credentials with customizable password rotation plugins and tools, enabling secure credential vaulting and distribution.
-
Embedded Password Management
Replace hard-coded credentials in applications, scripts, and tools—ensuring secure, dynamic credential management
-
Data Masking and Obfuscation
Privileged users only access the data required for their roles, minimizing the risk of sensitive data exposure.