Petro-CyberWorks Information Technology Co., Ltd. and Bamboocloud join hands to build a zero-trust benchmark case of Sinopec Group
Recently, Sinopec Group (hereinafter referred to as "Sinopec") demonstrated the network security operation protection capability of its key information infrastructure and the related construction achievements of smart industry at the "Light of the Internet" Expo in world internet conference in 2022. Through Sinopec's network security operation command platform, cloud security management and three typical network security operation management of zero trust and control systems, a systematic, normal and practical network security operation panorama was displayed.
Case background
In order to effectively implement the network security work in the process of digital transformation of enterprises, Sinopec put forward the vision of network security in the 14th Five-Year Plan, and built a network security capability system with dynamic integration and integration of attack and defense during the 14th Five-Year Plan period, which helped the new development of digital business of the Group and escorted the full realization of "building the world's leading clean energy chemical company". The Tenth Five-Year Plan proposes to build a complete trust chain of users, equipment, network and resources based on the concept of zero trust, aggregate security support systems and service capabilities, and take digital identity as the cornerstone, and conduct continuous trust evaluation and dynamic access control for business access.
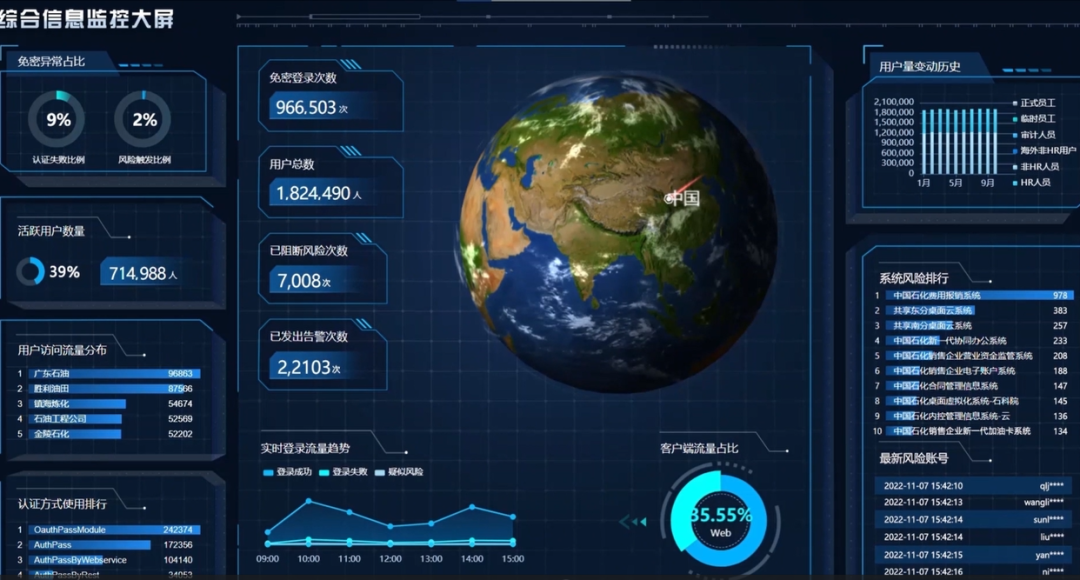
Construction content
Petro-CyberWorks Information Technology Co., Ltd. (referred to as "PCITC" for short) and Bamboocloud have established a set of continuous trust evaluation and dynamic access control system for Sinopec, which takes the unified identity IAM platform as the core cornerstone and integrates zero trust. For the application scenario of information access security in the energy industry, the core components of the zero-trust security protection system are combined with the zero-trust security protection ecosystem to provide trusted access, continuous authentication, trust evaluation and dynamic access control for users, infrastructure and business applications of the whole group. Trust evaluation and access control business scenario verification based on business applications, relying on zero trust security proxy gateway, unified application service publishing portal, realized asset hiding and reduced resource exposure; Carry out continuous identity verification for business access to minimize access authorization; Credibility evaluation of access behavior, dynamic generation of control strategy and fine-grained access control.
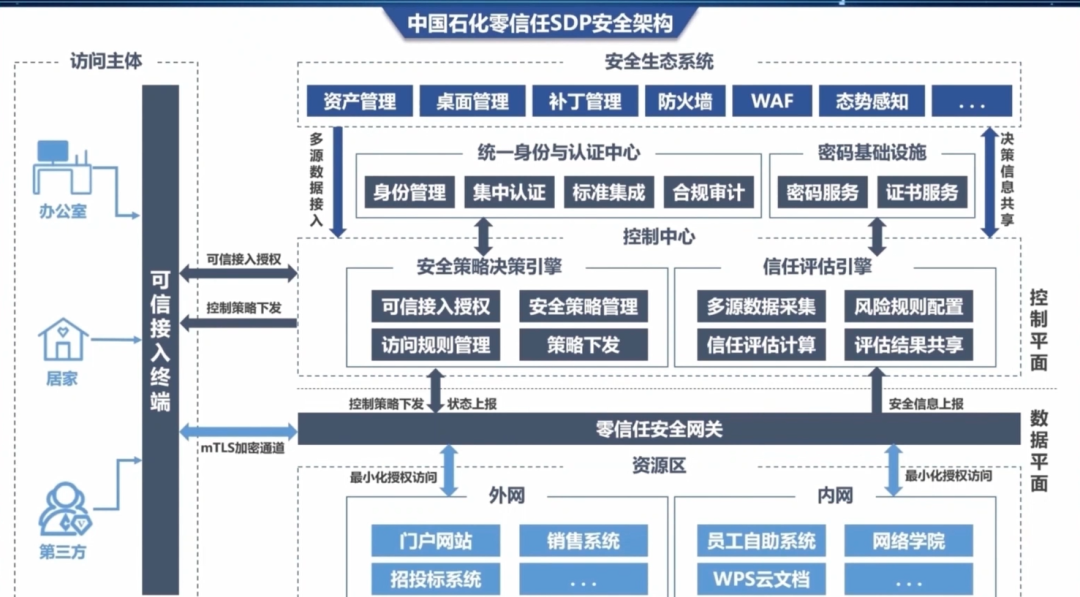
Case characteristics
No integration
Based on the IAM platform of the group, the system within the group has been integrated with it, and the application configuration access is supported. The gateway cluster and the application system network can be reached, which does not affect the deployment of existing application systems, without any customization or upgrade, and is convenient for rapid popularization.
No network transformation cost
The trusted control center (decision engine, trust evaluation engine) can communicate with the secure access gateway, which supports cloud deployment, does not affect the existing network structure, and does not need to make additional modifications, thus effectively reducing the IT construction cost of enterprises.
Configurable policy rule model based on ABAC
A policy rule model based on ABAC is established, which supports the multi-dimensional rule attribute of "subject, environment, object and behavior", multi-factor authentication, blocking, releasing, IP black and white list, user black and white list and message reminding rules of internal and external networks. It can be freely combined and configured according to security and business requirements, and can realize multi-scenario access control based on user, IP, application, menu, behavior and trust level.
Driving dynamic access control with continuous evaluation of trust
Through the continuous evaluation of trust level, the decision engine is driven to dynamically adjust the access control strategy to realize the dynamic control of business access. Risk calculation factors involved in trust evaluation support risk rule customization and combination association evaluation, and multi-source data can be accessed to realize flexible expansion of risk rule model and trust evaluation model.
Change from zero to whole and continue to trust
Zero-trust security leading practitioner









