Bamboocloud was selected in the report IDC MarketScape: China Zero Trust Network Access Solution, 2022 Vendor Evaluation
Recently, the international authoritative research institute released the report IDC MarketScape: China Zero Trust Network Access Solution, 2022 Vendor Evaluation (hereinafter referred to as "the report"), which provides reference for end users when choosing the technical service provider of zero trust network access solution. IDC conducted in-depth research on 24 representative technical service providers, comprehensively considered the existing capabilities and future strategies of enterprises in terms of products, markets and businesses, and demonstrated the comprehensive strength of zero-trust network access solution providers in China. With the comprehensive advantages of products, technology, market and strategy, Bamboocloud's zero trust security service platform and the overall solution are in the leading position in the quadrant of the reporting industry.
Comprehensive IAM+ continuous verification
Bamboocloud's Zero Trust Solution is a brand-new network security architecture with digital identity as the core and based on "continuous authentication and dynamic authentication". According to the multi-dimensional dynamic analysis of identity, equipment, network, environment, business access, etc., the authority and access behavior are controlled to form a new generation network security system with dynamic adaptive resource protection capability. It solves many security problems and challenges faced by current traditional protection methods, effectively protects the security of enterprise core business systems, and forms a complete zero-trust network access scheme. The overall solution has been successfully applied to customers in the government, finance, energy, construction and other industries, to protect the organization's information assets.
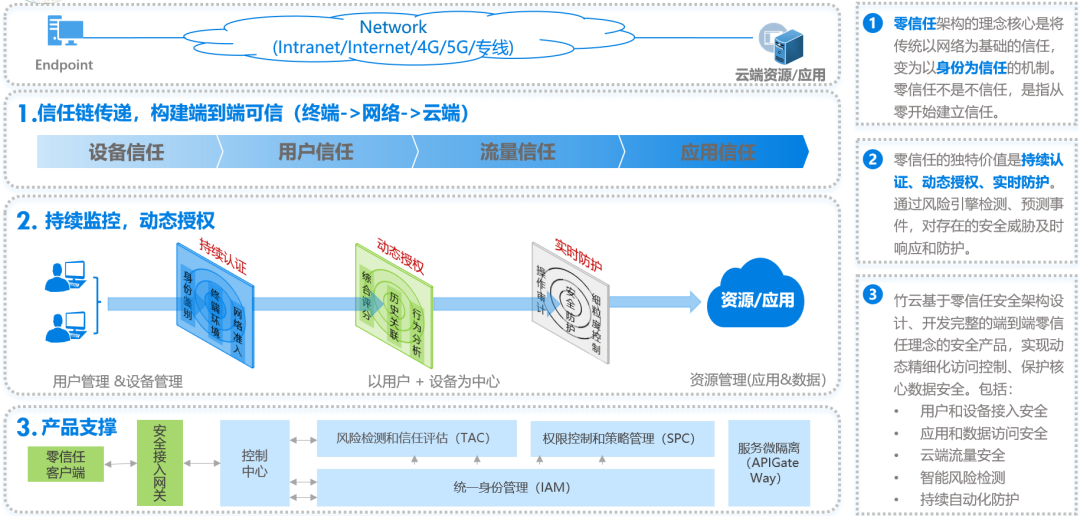
Based on identity, the access terminal and user identity can be trusted.
Give digital identity to the device, and ensure the trustworthiness of the terminal through a single package authorization mechanism. Based on IAM, the user authentication strategy in zero trust environment is constructed, covering single factor, multi-factor and other authentication methods. At the same time, users and devices are continuously verified through environmental awareness, risk detection and trust evaluation system.
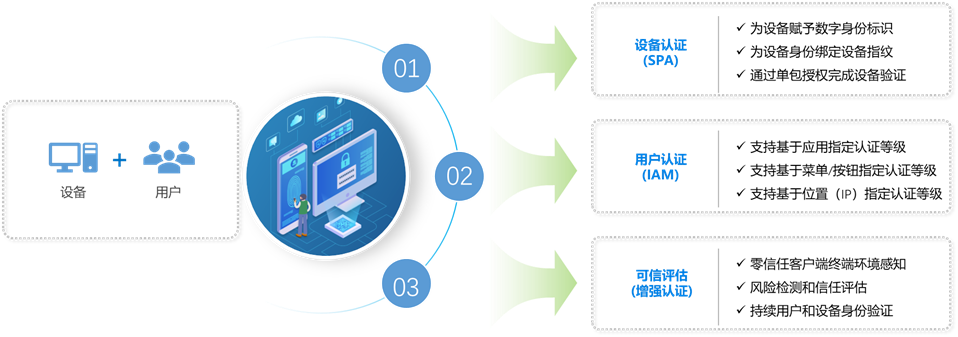
Strengthen traffic and application security to achieve secure business access.
Do not expose the access address and port of the enterprise application, completely hide the application server, and realize the network isolation between the application host and the external network. As the only gateway for enterprise application access, the security gateway hides the real host address and access domain address of the application, realizes zero-contact access, and eliminates all security risks caused by application exposure.
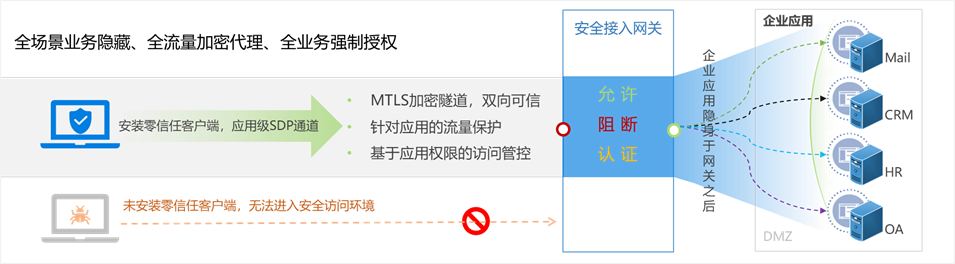
Real-time continuous evaluation, dynamic defense in depth
Every visit and even the terminal environment of a user needs to be detected and evaluated in real time, and the trust level of the user should be adjusted in real time according to the evaluation results. When the user's trust level drops, the user's authority is dynamically adjusted, or even the user's application access authority is closed to ensure the security of the application system. Establish an end-to-end complete trust chain of device trust, user trust, traffic trust and application trust through the secure access gateway, and realize end-to-end trusted access based on the security protection process of first authentication (authentication& authorization), then connection and re-access.
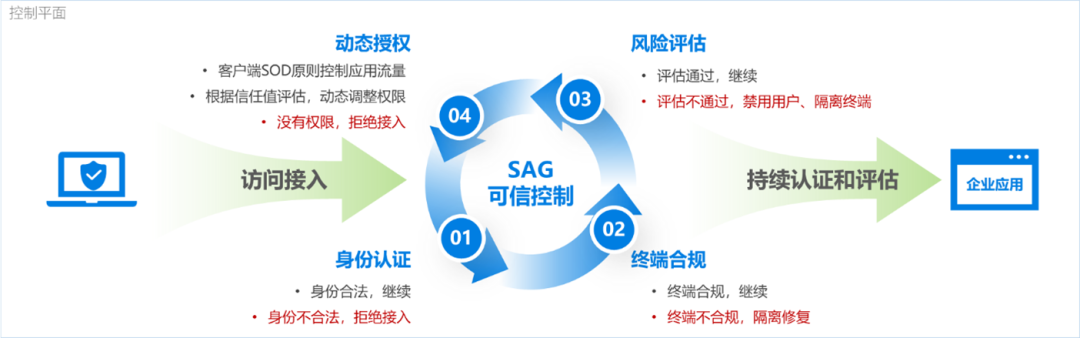
Refined dynamic access control
The platform provides IP-based and user black-and-white list policies, WAF-based traffic protection policies, and fine-grained dynamic authorization policies designed based on ABAC model, so as to realize integrated multi-source policy access and application access policy control.
Advantages of products and solutions
Meet SDP model requirements.
Through Bamboocloud SAG products, application systems are hidden and protected from external security threats:
A single package SPA authorizes the establishment of trust connection with SAG
Realize the authentication and authorization of users and devices
Two-way encrypted communication to ensure the security of data transmission
And hide the connection between SAG control and management application visitors and application systems
Protect investment, upgrade organizational security architecture at low cost.
Through the programmable capability of SDP controller, the integration and cooperative work of the existing security control systems of the enterprise are realized, including the original IAM system, EPP/EDR system, authority control system, etc
No application transformation cost









